Google at loggerheads over support for journalism
Google and the state of California have come to loggerheads over legislation designed to require Google to provide financial support for local journalism. Naturally, Google is fighting this with a PR and lobbying blitz. They and their allies may be missing the point. Whatever the outcome, it could have a profound impact on the democratic process. The legislation, The California Journalism Preservation Act (CJPA) has been wending its way through…

R.I.P. Kevin Mitnick
One of the most famous – or infamous – hackers of all time, Kevin Mitnick, passed on July 16th.
While early in his career he was definitely leaning towards the dark side, he later did more for raising awareness to cybersecurity threats than most people.
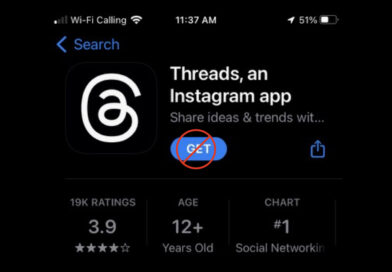
Meta’s Threads threatens personal security for women seeking abortions
Company is a ‘paid informant’ Threads, Meta’s new microblogging platform, could be considered a clear and present danger to women in the US seeking abortions in states where abortion access has been severely restricted. At the same time, it could

Credential Harvesting: Understanding and Combating the Threat
In the growing battle against cybercrime, digital identities have become an increasing target for cybercriminals As a result, credential harvesting has emerged as a dangerous security risk.
Features
Company News


Advertisement
Support Us
How about you buy us a coffee?
Newsletter
Read our archived Newsletters here.
Podcast

Murky third-party agreements weaken healthcare privacy controls
The healthcare industry is a vulnerable target of cybercriminals, but not for the reasons most business sectors are. Between 80 and 90 percent of all cybercrime results from people not following basic cyber hygiene practices, but in healthcare criminals gain access to information through infrastructure weaknesses and the murky third-party agreements.
Latest Video
Articles

Not if, but when: Why it’s time to prepare for the quantum threat
In recent months, the drumbeat of warnings about the quantum security threat has reached an alarming crescendo. For a reason: the encryption standards we rely on today are at serious and imminent risk.
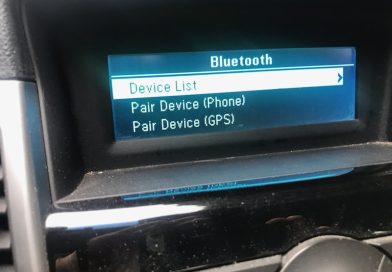
Stalking with Bluetooth tracking devices
Technology companies traditionally ignore the safety downsides of their products. Bluetooth tracking devices can surreptitiously shadow people. But it’s easy to disarm them.

Patching in the Modern Organization: Why a Key Security Control Is Still Overlooked
This article provides an in-depth analysis of what is keeping organizations from establishing a solid patching program and offers practical tips for overcoming those challenges.

Retrospective: praise for the cybersecurity experts out there
In 2021 the worst case scenario of broad outages or mass ransomware attacks didn’t happen if it weren’t for the work of one very special group of people: cybersecurity experts. A big thanks to all of you from Cyber Protection Magazine!

Predictions Finale: Legislation, standards drive chip security in 2022.
Finishing up our series on 2022 predictions we went to some of the people we’ve talked to in the past year to get their views on what will influence chip security for the positive in 2022.

5 Tips for Industrial IoT Security to Defend Against Cyberattacks
Ransomware is giving way to the even higher stakes of killware for critical infrastructure. Hits on industrial IoT in critical infrastructures are becoming less about money and more about control and causing as much damage as possible.

Lawsuit Pulls Back Curtain on Quantum Crypto Industry
The benefits of quantum computing are a bit hazy, but the danger of the technology is significant. Nation-states are pushing hard to develop quantum computers primarily to break the strongest encryption codes available. That makes governments, infrastructure organizations and corporate

Scam Bucket: Latest Russian Phishing Scam
The Russian cyber offensive against the West finally hit last week and it was a pretty weak phishing scam.

4 Tips to Meet Cyber Insurance Requirements
If you’re looking to meet requirements and save on cyber insurance premiums, focus on lowering your risk profile. Here's how.
This content requires that you purchase additional access. The price is $1.00 or free for our Premium members.

Video Bytes: Changing the Script on Cybersecurity Hiring, part 3
In our thrid episode with Matt Donato we look at the candidate experience in the hiring process; where it goes right and where it goes wrong.

Identity Management Day 2022: Time to Be Identity Smart
Today is Identity Management Day. With 79% of all organisations having experienced an identity related security breach, this is an issue that must be taken seriously.