Poor marketing endangers society
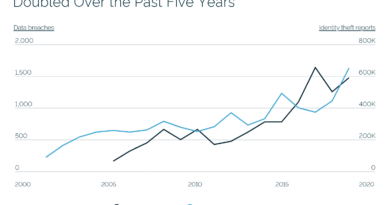
n the past few weeks, as various security companies have published multiple studies about the state of cybersecurity, a common theme has arisen: Executives running the companies that purchase security tools and services are not sure their purchases have made them any safer. This widespread position in the market confirms results of a months’ long investigation by Cyber Protection Magazine that marketing practices in the industry are failing to do the job and, in the process, making society less safe.
While every report skews data to convincing customers to add their company’s tools and services to their budgets. However, every report also reports that between 60 and 90 percent of managers have significant concerns and doubts that the tools they have, and the tools they are considering, will not do the job that needs doing. The reasons for that lack of confidence are three-fold.
Three reasons for lack of trust
First, stuff is moving fast. Governments are legislating controls and protections faster than normal. Sometimes this rules don’t make sense and many in the industry think they are holding back innovation and adoption. Criminals and nation states are stepping up attacks that bypass established protections, and lawsuits for negligence are growing. Second, while understanding the need for security best practices is at an all-time high, that’s mainly because weaknesses due to work-from-home, generative AI and news about data breaches is also high. That means while understanding of the need is high, inexperience and ignorance is creating new opportunities for attacks.
“Many executives may not exactly understand how (the tools) work,” said Cache Merrill, founder of software outsourcing company, Zibtek. “. When there is a concern on the functionality of the tools or when attention is on what the tech teams understand without listening to them, anxiety is experienced. To put it simply, if they cannot see it, they will not put faith in it.”
Carl DePrado, an SMB IT consultant based in New York, aid, “The sheer number of cybersecurity products and services can be overwhelming. This contributes to a sense of vulnerability, as they may not feel confident that they have covered all their bases.”