With this article, we’d like to share some detailed tips on how you can secure your home network to assist corporate IT security in preventing potential cyber threats.
These days, with more and more people working from home, insecure home networks are opening up possibilities for hackers so also get access to corporate networks. After all, corporate networks have an entire IT or even IT security department which protect them against attacks through different technologies. Thankfully, those IT guys know what they are doing and know what’s best to secure the infrastructure they are responsible for. But you don’t need a security expert to do secure your network at home. With just a few tips, most potential attacks can be prevented.
Tip No. 1: Wifi key
The encryption of the Wifi connection at home is now standard and comes predelivered on most routers. However, many of these preset keys consist only of digits – with tools that can be easily downloaded from the Internet, such a key can be cracked in a few minutes. Accordingly, the first thing to do is to change this key and choose a password that consists of a combination of digits, upper and lower case letters and ideally special characters. There is no need to choose a combination that is difficult to remember. Instead, the longer the password, the more difficult it is to crack. For example, more or less nonsensical sentences have proven themselves. For example, the sentence “Rabitsweartrouserswheneveritis20degrees!” is hardly crackable even with a supercomputer – but still relatively easy to remember.
Tip No. 2: Change passwords
Nowadays your wifi at home not only consists of the router and your laptop – there are many more different devices connected to the internet. For example, a smart home consists of many different devices – smart lights, smart TVs, cameras, baby phones – the number of Internet-enabled devices is growing rapidly. Each one comes with its own user interface or app. While most devices are now protected by a username and password, far too often they consist of easy to guess combinations – with the username “admin” and the same password you will be able to control many of these devices. These devices are also often accessible from the Internet – after all, you want to be able to see who is at the door, even if you are not at home. For hackers, this is the equivalent of an open front door. Cyber criminals have a big advantage here: the “open front door” can be found on the Internet with just a few clicks. There is even a special search engine that lists smart devices accessible from the Internet.
Hence it is easy for hackers to control smart home devices and thus gain access to the home network. Even if you want to get such a device up and running as quickly as possible, you should take the time to change the default password. The above mentioned tips for password security apply equally.
Tip No. 3: Splitting networks
If an attacker succeeds in gaining access to a device, the damage remains limited if the acquired device is not in the same network as your laptop you use for work. This sounds complicated, but in most cases it is not. Most routers now offer the possibility of setting up a so-called guest network. This is separate from the “normal” home network – devices in this network cannot access the home network, but are still connected to the Internet. Thus, even if a camera is compromised, the PCs and smartphones – and especially their data – are not at risk. For the same reason, it is also recommended to grant access to visitors’ devices only for the guest network.
Some routers also offer the option of setting up additional networks. Although this is often associated with greater effort, it is particularly useful if you work from home regularly. This way you can additionally secure access to your company’s network. Those who are not afraid of setting up the system can take the whole thing to the extreme by defining several networks for different applications – i.e. in addition to the network for the home office and that for the private computers, for example, a special network only for the smart home.
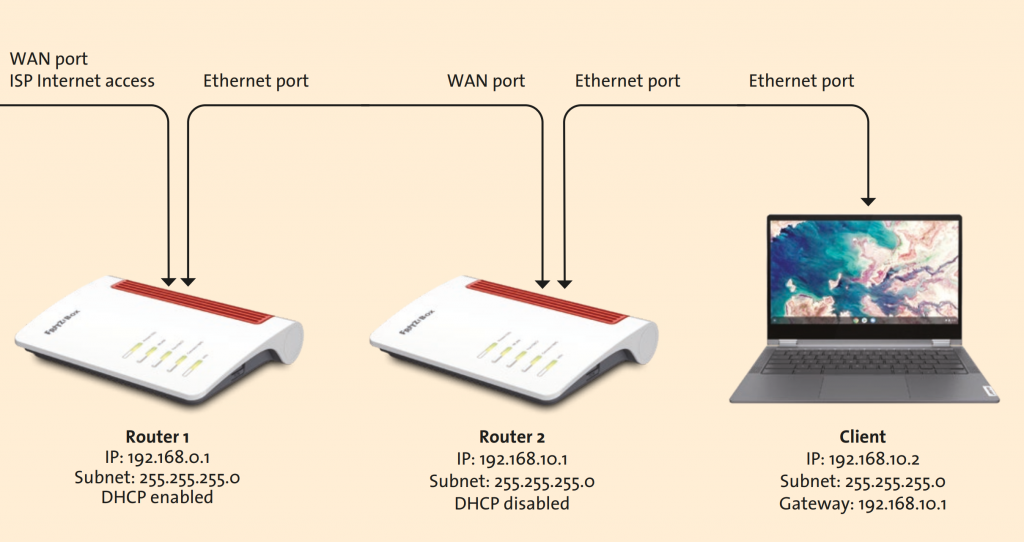
Tip No. 4: Router Cascade
Simply put, a router is used to connect the various devices on a home network to the Internet. Just like in a medieval city, the router is the gate the outside world. Actually, many router today are now equipped with security functions and – to stay with the picture – also function as city walls or gatekeepers. However, some of the examples mentioned here show that there are still loopholes. So what could be more obvious than to simply build a second wall?
Source: Plugged Media // Smart Homes
In network jargon, this is called a router cascade. This offers another advantage: Devices behind the inner wall can get out at any time, so they are still connected to the Internet. All devices behind the outer wall can also access the Internet, but they cannot overcome the inner wall. Setting up a cascade of routers is less complicated than it may seem at first glance. In addition to the router that provides Internet access, you need a second router that in turn spans the home network. It is only important that both routers use a different address range for their respective networks. To illustrate this with an example: The “inner” router can be reached under the IP address 192.168.0.1. The last number represents the address range of the home network. A PC connected to this router could therefore have the address 192.168.0.2. The outer router, in turn, can be reached at the address 192.168.10.1 – and thus is in a different address range. If the PC is now connected to this router, it has the address 192.168.10.2.
Tip No. 5: Special products
Of course, manufacturers have also recognized that securing the home network is important. However, the last two tips in particular require at least a basic knowledge of network technology, even if the setup for private users is quite possible. Many router manufacturers have therefore switched to integrating as many security functions as possible directly into their devices. For example, many routers will notify you when a new device registers in the home network. Even a rudimentary firewall to ward off the most common attacks is now included in many routers. These functionalities already offer a certain basic protection.
If you want to play it safe, you can also use devices that are specially designed to protect your own network. F-Secure, which provides security solutions for home and business users, has developed F-Secure Sense, a router that protects all Internet activities in the home. It blocks harmful websites and other threats and protects all smart devices from cyber attacks. A subscription ensures that the latest threats are always included. The Fingbox works in a similar way, proactively informing the user about security risks such as new, unknown devices or loopholes in the home network. Although the protection is less comprehensive here because a database of threats is not used. There is no need to subscribe to it and after the initial installation, the Fingbox works largely in the background and only reports when there is a real problem.
Security has priority
No matter which way you choose, securing the home network should be a matter of priority. You can read it almos daily in the media: successful attacks are no longer the exception but the rule. Anyone who has been affected by such an attack knows that the damage caused by a cyber attack is not only comparable to a “real” burglary, but often goes beyond that. Everyone should be able to implement the first two tips in this article and do so immediately. If you don’t feel confident enough to implement the other tips yourself, you should hire a specialist – the costs involved are always a good investment.
Patrick Boch has been working in the IT industry since 1999. He has been dealing with the topic of cybersecurity for several years now, with a focus on SAP and ERP security.
In recent years, Patrick Boch has published various books and articles as an expert, especially on the subject of SAP security. With his extensive knowledge and experience in the areas of SAP compliance and security, Patrick Boch has served as product manager for several companies in the IT security sector since 2013. Patrick is Co-Founder and Editor of Cyber Protection Magazine.




Pingback: Fraud Alert! 4 Common Business Scams (And How to Protect Yourself)
Pingback: Video: USB Ninja with Kevin Mitnick - Cyber Protection Magazine
Pingback: 3 advanced ways to securing your home and business - Cyber Protection Magazine
That’s quite informative, you just told me all the cybersecurity problems and it’s solutions. These days we are facing more cases of hacking than robbery. That is why we need to improve our home Security Network.