A few weeks ago, marketing departments for cryptography companies went into overdrive. The National Institute of Science and Technology (NIST) announced four algorithm standards to protect against quantum computing hacks. At least 17 companies (by our count) put out press releases insinuating they developed one or more of them. That insinuation is false so Cyber Protection Magazine decided it’s time to start demystifying quantum cryptography.
Quantum computing is a technology that 99 per cent of the population will never interact with but should be concerned about. The computers we know today have chips with millions of silicon switches (transistors) that are in two states: on or off. The pattern of all these switches determines the data. Quantum computers, however, operate on a new type of semiconductor material where spinning electrons can be in either state at the same time, like Schrödinger’s cat. That means the quantum computer can process mathematical problems much faster than any digital computer.
That’s a good thing when you are creating AI-based robots or calculating data back from a deep-space telescope. It’s a bad thing when nation states use quantum computers to crack high-level encryption to steal data and take over computerized control systems protected by current encryption standards.
Standards are falling
Those standards are, for the most part, RSA (named for Rivest, Shamir, and Adleman, the developers of the encryption), which was developed 50 years ago. The other, lesser-used is elliptical curve cryptography. ECC is faster and easier to use, but RSA has been around longer and therefore has greater distribution. These standards have stayed in place because it takes supercomputers decades or centuries to brute force their way through. But quantum computers can break them in seconds, hence the cause for concern.
Literally, billions of devices, data centres and even supercomputers are vulnerable to quantum computers in the hands of the wrong people. Currently, the United States is leading in the development of the technology, followed by Canada (yes, Canada) and then China. Israel has also had a few breakthroughs in development, however, all of the work is still mostly theoretical. But the very real developments mean we need quantum cryptographic protections now. Thankfully, it seems that development is moving faster than quantum computers.
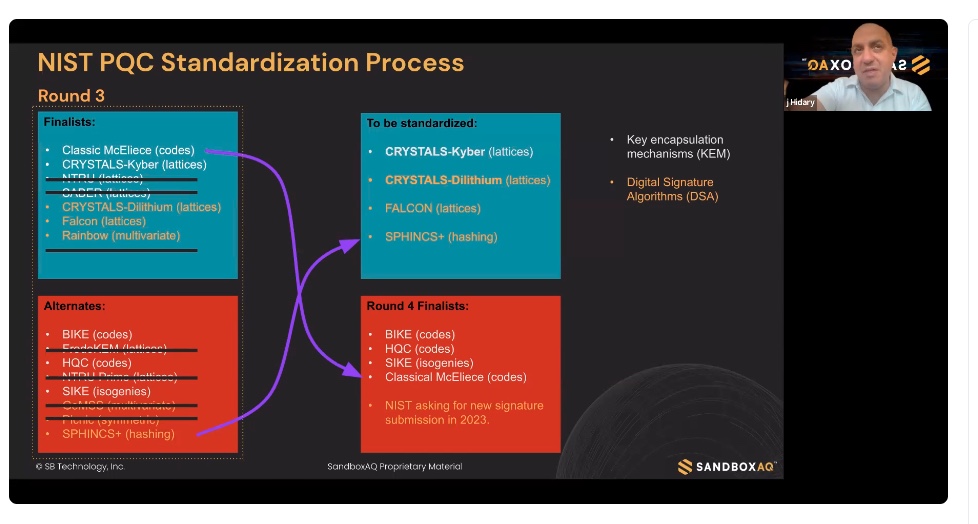
Hundreds of companies of computer science researchers have been working on dozens of cryptography algorithms. With the NIST announcement, they are ready to productize while investments in cryptography start-ups have increased. The flood of press releases following the NIST announcement is a collective wave of relief from those companies that participated in the development of the four and had not wasted time on something else.
“We definitely contributed to all four of them,” said Alan Grau, vice president of business development for PQShield, one of the startups involved. “Obviously, other companies have contributed to these algorithms as well. We’re a company with commercial intents and VCs that want us to sell lots of stuff. So we’re gonna build whatever NIST says. But, yeah, we were happy that we’ve concentrated on the four selected.”
Post Quantum Cryptography
PQShield and dozens of other companies offer post-quantum cryptography (PQC), sometimes also referred to as quantum-safe computing. However, getting every device and network protected from quantum-computing attacks is going to need every one of those companies and probably more, to convert every device and system from the old RSA/ECC encryptions. That reality is made more difficult by the fact that it is almost impossible to find every instance that needs converting.
A new entry, SandboxAQ, has a set of tools to make that easier, according to Jack Hidary, CEO. SandboxAQ was spun out of Alphabet early this year.
“We have an analyzer that finds and tags all these instances within a network. In a large bank, you can be talking about as many as 50,000 instances using old software and protocols. Second, our benchmarking software analyzes the new PQC protocols identified by NIST to see what impact they have on the performance.”
The final tool, Maestro, helps implement the new cryptography across all instances, Hidary explained. “We’re moving into an era that goes from a single standard, essentially RSA, to a multi-pronged standard. Maestro uses built-in machine learning to make real-time decisions as to which standard you would use in that instance.”
SandboxAQ also provides an AQ Virtual Private Network (VPN). It is already replacing VPNs for Softbank Mobile in Japan, Vodafone in Europe, and other telcos around the world.
Hidary recommends anyone considering changing telco providers in the next few months should ask whether they are PQC compliant.
Related:
Redundancies needed
Another player in the niche, Quantum Xchange, provides the means for proliferating the new cryptography through a network, like SandboxAQ, but they also provide redundancy.

Dr. Vincent Berk, chief revenue and strategy officer for Quantum Xchange, said researchers broke several candidates for NIST approval within hours by conventional computers. He asserts that no one knows if the PQC algorithms will be as impenetrable for as long as RSA was (50 years). “How can enterprises remove a single point of failure in their cryptography if their only choice is a single, vulnerable algorithm?”
As a result, QuantumXchange creates a second cryptographic “tunnel” based on the RSA standard or optional second PQC at each point.
Cryptography standards have remained viable for 50 years but they are also static, The new standards may not last 10 years. But we don’t have 50 years to make them standards either. Companies like PQ Shield, SandboxAQ, QuantumXchange, and hundreds of others are needed to keep us up to date. Definitely a growth industry.
Lou Covey is the Chief Editor for Cyber Protection Magazine. In 50 years as a journalist he covered American politics, education, religious history, women’s fashion, music, marketing technology, renewable energy, semiconductors, avionics. He is currently focused on cybersecurity and artificial intelligence. He published a book on renewable energy policy in 2020 and is writing a second one on technology aptitude. He hosts the Crucial Tech podcast.



Pingback: Demystifying Quantum Cryptography | QuantumXC