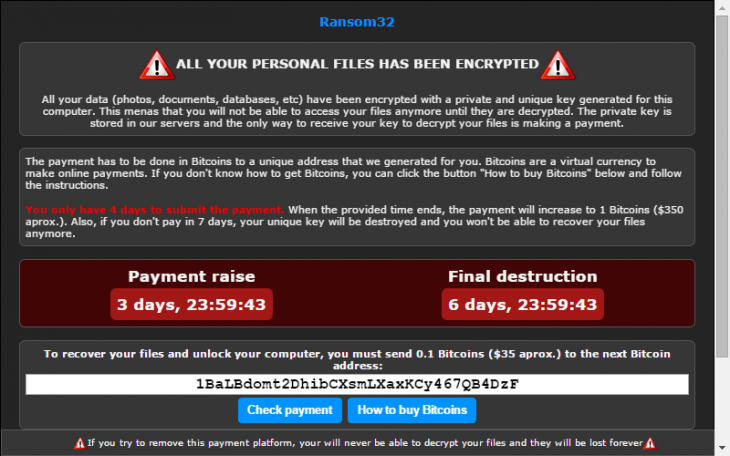
Even seven years on, the name WannaCry still invokes memories of chaos and disaster amongst anyone in the technology world (and many more outside of it, too). In a very short space of time, the ransomware worm spread to over 200,000 computers in over 150 countries, shutting down organisations from FedEx to the UK’s own NHS.
The anniversary of this widespread attack in May each year has been named Anti-Ransomware Day, to encourage organisations to back up their data and adopt necessary security protections to help prevent ransomware from having a potentially devastating impact such as this.
We spoke to eight experts in the technology industry to find out what ransomware looks like today, how to defend against it, and what the future holds.
Ransomware in the present day
While ransomware may have been around for decades, the way in which cyber criminals use it to their advantage has changed dramatically over the years. As Andy Swift, Technical Director of Offensive Security at Six Degrees, explains: “Several years ago you could reliably identify how certain groups would approach gaining an initial foothold on a target network: there would be documented kill chains that you could follow end-to-end describing patterns of entry, pivoting, lateral movements, exfiltration, deploying encryptors, and so on.
“While these still exist and ring true in many cases today, what is showing signs of change is the frequency at which attackers are turning to bleeding edge or zero day exploits as a more dynamic method for gaining footholds. Proof of concept code for new exploits today is simply being turned around faster than ever and, combined with new research suggesting that exploitation of vulnerabilities as an entry point for a breach increased by 180% between 2022 and 2023, paints a picture of the changing tide.”
Chris Denbigh-White, CSO at Next DLP, agrees that ransomware gangs have escalated their tactics in recent years, “by [also] engaging in multifaceted attacks involving encrypting and exfiltrating data and leveraging this information to coerce victims into compliance. This advanced attack level extends to disclosing the breach to victims’ customers and regulatory bodies if ransom demands are not met, thus extending the ultimatum to ‘pay us or we will release your data AND report you!’
“Over the past few years, ransomware particularly has followed a ‘SaaS-like’ model, which has seen a move from individual gangs conducting individual attacks to ‘criminal service providers’ offering infrastructure, payment services, and software licensed to conduct multiple operations across many sectors.”
“Therefore, identifying and remediating vulnerabilities that ransomware groups may be able to exploit must be a key priority for organisations,” advises Nick Palmer, Solutions Engineer at Censys. “However, this is easier said than done, as very few organisations have a comprehensive view of their potentially vulnerable assets. Attack surfaces have grown beyond what traditional security practices can effectively manage – in fact, on average, 43% of assets on an attack surface are unknown to organisations. This is crucial because you cannot protect what you cannot see.”
So what can be done?
Four steps organisations can – and should – take
- Get the basics right, says Martin Simpson, Principal at Node4 Security Practice
“Enhance your defences with good and actionable threat intelligence, and robust monitoring to detect malware before it detonates. It is also important to conduct regular vulnerability scanning and remediation. Understand what your important data is, both in structured and unstructured forms, and protect it accordingly. Doing the basics well helps you understand what your important data is and where it resides so that you can apply the necessary protection.”
- Prioritise tailored cloud-native defence, recommends Moshe Weis, CISO at Aqua Security
“We recommend prioritising the adoption of proactive measures and robust defence strategies tailored to cloud-native environments. This includes deploying advanced endpoint protection solutions integrated with Secure Access Service Edge (SASE) capabilities, implementing micro-segmentation and network segmentation to limit the lateral movement of ransomware, ensuring regular data backups stored securely in cloud repositories, and conducting comprehensive employee training and awareness programs.”
- Have a clean recovery environment, suggests Darren Thomson, Field CTO EMEAI at Commvault
“In order to stay one step ahead, every organisation should have a clean environment (a “cleanroom”) into which they can recover. Partnered with automation technology, critical cloud applications can be rebuilt in the designated cleanroom quickly, taking recovery time from days or weeks to a matter of hours or minutes and enabling organisations to return to minimal viable operations, even when systems are compromised. Through the power of the cloud and AI, this is now possible at a low cost and in a scalable manner, making it accessible for every organisation, no matter their size or maturity.”
- Utilise third parties carefully, adds Six Degrees’ Swift
“Organisations must ensure they have enhanced data protection through authenticated data access, data encryption, and solid data backup solutions. And this requirement should extend through their suppliers and partners – using zero trust practices, least privilege access, and boundary controls all the way down the supply chain.”
United we stand
But the fight against ransomware can’t be won by individuals alone – organisations must work together as a united front. Jason Keirstead, Vice President of Collective Defense at Cyware, reveals how “a collective approach to cybersecurity can transform this landscape and fortify defences against ransomware.
“Ransomware is different to a targeted APT or spear-phishing campaign because the malware that is used is not new or unique to each attack. If one organisation then develops a technique for detecting a specific form of malware, this is invaluable information for many other IT security teams. But, this valuable insight is rarely shared outside of the organisation that discovered it. This gives attackers a huge advantage because the one thing they have in their arsenal that security teams often don’t have is a collaborative approach.”
He explains: “By adopting a collective cyber defence strategy, organisations can collaborate internally within teams, and externally across industries to share this valuable insight and defend against cyber threats including ransomware.”
Is a payments ban on the table?
With these measures in place, organisations will be in a much stronger position to both prevent and recover from ransomware attacks. But if that’s the focus here and now, what does the future hold?
Laurie Mercer, Security Architect at HackerOne, asks: “With a record low of ransomware payments witnessed, does this highlight a possibility that organisations are now prepared for an enforced payment ban? Enforcing a ransomware payment ban is like banning smoking – you know it’s good for society in the long run but in the short term, it is difficult to stop getting a quick fix. UK organisations should be better prepared than most to enforce a ransomware payment ban due to their lead in the field of cybersecurity and cyber security services like insurance products.
“The pros of banning ransomware payments are that it removes an incentive for criminal activity and is a morally sound choice. The cons are that in the short term, this will result in an increase in data breaches, PII leaks, and the destruction of hardware and software assets when the payment demands are not met. The reality is that whilst the UK is a leader in the cyber security industry, many many organisations lack the resources to defend against these attacks.”
So will we see a ransomware payments ban? Maybe, maybe not. But after the advice being shared widely thanks to Anti-Ransomware Day, hopefully what we will see is organisations taking a new approach to protecting themselves and their data, and a future with a little less ransomware in it.