Virtual reality always appears to mirror the reality that’s on the ground and the turbulent year of 2020 was, unfortunately, no exception. From 2019 to 2020 there was a distinct rise in the amount of malware that was executed, which is all the more visible when analyzing the progression from month to month. This rise was seen across the different malware types, from ransomware and spyware to droppers and miners. However, not only did 2020 suffer from more malware attacks, but the sophistication and daring of threat actors also grew, evident by the financial damage inflicted on organizations as a result of these more cunning attempts.

How COVID19 Played into the Hands of Hackers
Like any criminal underworld, the hazards of 2020 represented numerous opportunities to cyberthreat actors. The Coronavirus pandemic which caused companies around the world to suddenly switch to a work-from-home module, inadvertently widened the attack surface of organizations. Employees were no longer working from behind the safe confines of the corporate network.
Moreover, the pandemic, the US Presidential elections as well as the Black Lives Matter movement, were some of the hot topics that became the “cover stories” in many phishing campaigns. The dropper documents accompanying these phishing campaigns were used to distribute secondary malware samples, such as worms, spyware and ransomware. Their objective was often the theft of Personally Identifiable Information (PII) and their efforts proved to be successful, potentially even beyond the expectations of hackers themselves.
Top 5 Malware Families
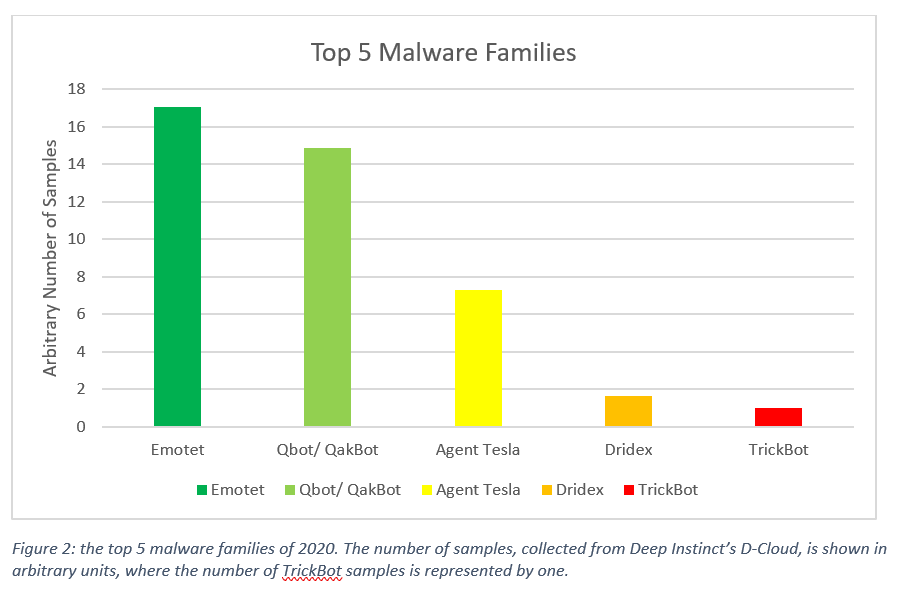
Emotet was one of the most prevalent financial malware and botnet threats this year. It first appeared in German speaking countries in Europe around mid-2014, and after two years without significant activity, Emotet reappeared in 2017 attacking ever since, targeting the UK and the US. From its very first version Emotet spread mainly via spam campaigns, imitating financial statements, transfers and payment invoices. Once it is dropped and run, Emotet intercepts and logs network traffic, injects to browsers and tries to access banking sires, to steal and store financial data. In its later versions, Emotet has evolved into a botnet that drops other malware into the victim computer once initial access is achieved.
Qbot, the second most prevalent form of malware, is a popular info stealer and banking malware that has been active in the wild since 2009. Its main purpose is to steal online banking credentials and other financial information, though Qbot can also steal additional personal data, such as files, and keystrokes. Additionally, Qbot possesses worm features allowing it to spread through network and removable drives.
Qbot monitors the browser on the infected machine to detect when victims interact with an online banking website, in order to steal credentials. Additionally, Qbot collects further information from the infected machine including IP address, origin country, cookies and other system information.
Qbot’s distribution methods vary and include malspam with specially crafted document attachments triggering the infection. It also uses exploit kits that are deployed on compromised websites that delivers Qbot’s payload to a website’s visitors.
Top 5 Ransomware Campaigns

The most prevalent malware detected by Deep Instinct’s Threat Intelligence Researches was Sodinokibi. This ransomware first appeared in the wild shortly before operations for Gandcrab ransomware ended in April 2019. Sodinokibi has since been involved in several high-profile targeted attacks, mostly against companies and government organizations.
The hackers developing and spreading the ransomware have used several different tactics in their attacks, including use of zero-days, Powershell scripts, targeting of large corporations, and in some cases have also successfully conducted completely file-less attacks.
Ryuk another high performer in the past twelve months, has been involved in numerous targeted ransomware attacks, including several high-profile ransomware incidents, such as attacks against Florida municipalities, which netted the criminals tens of millions of dollars.
When Ryuk infects a system, it kills over 40 processes and stops more than 180 services, before beginning to encrypt files. Additionally, Ryuk requires Admin privileges to run and maintains persistence by writing itself to the Run registry key. Several updates of Ryuk have appeared since its release, and in its latest update, in September 2019, Ryuk was programmed to steal confidential military, financial, and law enforcement files.
These research findings along with a wider analysis of developments observed in 2020 can be found in Deep Instinct’s threat landscape report. The report discusses trends seen during 2020 and provides concrete data to verify the credibility of these developments.
Shimon is a cyber security expert with experience in research and operations, both offensive and defensive. Prior to joining Deep Instinct in 2016 Shimon served for 14 years as an officer in the IDF’s elite cyber unit 8200. Shimon’s background includes a wide range of cyber security and research positions, where he managed multifunctional teams of hackers, researchers and engineers. Shimon led the development of new methods and tools for the analysis of cyber-campaigns, as well as a series of innovative cyber intelligence collection capabilities. Over the years Shimon has worked extensively with a variety of industry, defense and intelligence partners and agencies in North America and Europe. He is a recipient of the President of Israel Award for Outstanding Military Service, holds a B.Sc (Magna Cum Laude) in Electrical Engineering from Ben Gurion University and MBA (Cum Laude) in Finance and Accounting from Tel Aviv University.

