In the immortal words of Ferris Buller, “life moves pretty fast.” This is particularly true for the technology landscape and the related aspects of cybersecurity, which accompany tech. Recently, the OCEG published, The Ultimate Guide to Information Security & Continuity – Things to Know and Places to Go (“OCEG Ultimate Guide”), which is a substantive resource focused on Information Security Programs (“ISPs”). The purpose of this article is to highlight some of the key aspects in the context of other regulatory developments and court cases.
Analysis
When considering governance, risk management, and compliance (“GRC”) in addition to the National Institute of Standard and Technology (“NIST”) Cybersecurity Framework 2.0 (“CSF 2.0”), the OCEG Ultimate Guide provides practical considerations. These resources can be utilized to reduce cybersecurity risks associated with GRC.
Before delving into OCEG Ultimate Guide, the revised Core illustrates the shift from cybersecurity (protecting data) to cybersecurity risk management with the addition of “govern.” NIST’s existing CSF had five core functions, which remain in CSF 2.0 – identify, protect, detect, respond, and recover. Governance is the top function because the Framework Core Functions are organized at their highest level – spans across the entire organization, both vertically and horizontally.
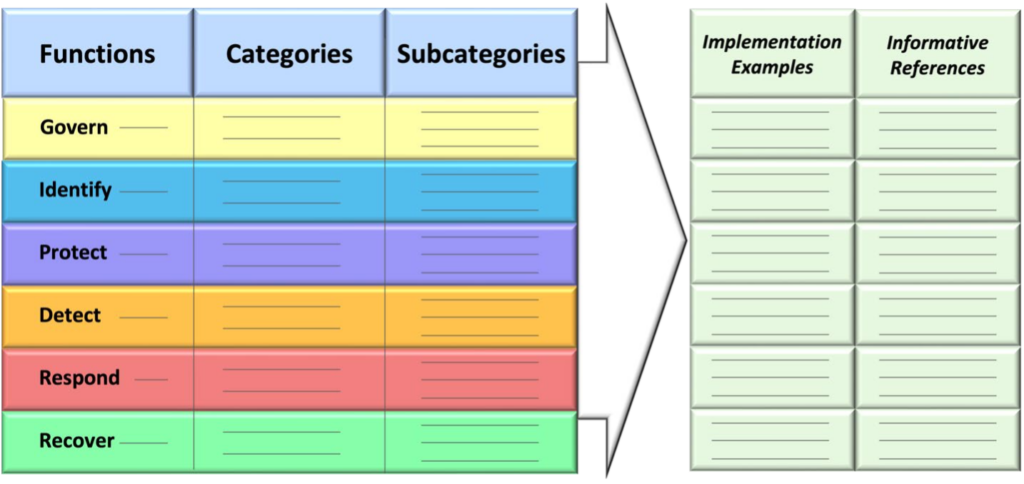
How does this Framework Core meld into the OCEG Ultimate Guide? As part of this “infomercial” – the OCEG Ultimate Guide’s objective is to offer a flexible approach to four main areas:
- core knowledge;
- organizational GRC capabilities;
- leading practices; and
- useful resources.
By continuously evolving as the threat landscape shifts, planning for implementation, while remaining nimble enough to adapt to sudden changes, and keeping up with technology trends, cybersecurity risk management across any organization remains relevant.
A fundamental proposition posed in Chapter 1 is “Why Information Security Matters.” Given the United States Securities and Exchange Commission’s recent Cybersecurity Final Rule, which became effective on September 5, 2023, the following passage from Chapter 1 is apropos:
The growing importance of information security has led regulators to publish addition guidance and new requirements, further expanding the already extensive regulatory ecosystem related to information security and continuity. National regulators worldwide consistently issue new regulations covering a wide range of topics, defining roles and responsibilities, and emphasizing incident event disclosure. Industry-specific regulatory efforts are also substantial, addressing sectors such as financial services, critical infrastructure, healthcare and transportation.
Beyond regulatory compliance and corporate reputation protection, there is a growing recognition that information security is vital for the success and continuity of business operations, particularly during cyberattacks, natural disasters, or system failures. Robust security controls minimize the impact of such incidents, reduce downtime, and enable quick recovery to resume normal operations. This contributes to overall business resilience planning and risk management.
Stated another way, Business Continuity and Disaster Recovery Policies and Procedures should center around the aforementioned items which make information security vital to any organization’s well-being. Security and continuity capabilities are vital to protecting data assets and IT infrastructure. Achieving “Principled Performance” can be done through integrating a proactive approach by addressing these six areas:
- Governance & Oversight
- Strategy & Performance
- Risk & Decisions
- Compliance & Ethics
- Security & Privacy
- Audit & Assurance
Hence, “considering the role of information security within the organization’s overall GRC efforts is a key step in this process.” What are some of the benefits to adopting GRC? As set forth on page 14 of the OCEG Ultimate Guide,
- Alignment of objectives: The GRC Capability Model ensures that information security and continuity efforts are aligned with the organization’s overall strategic objectives. By integrating GRC principles into the program, organizations can effectively prioritize their security and continuity initiatives, allocate appropriate resources, and align them with the organization’s risk appetite and business goals.
- Holistic risk management: GRC provides a comprehensive approach to risk management, enabling organizations to identify, assess, and manage risks comprehensively. By incorporating GRC practices into the information security and continuity program, organizations can systematically identify potential threats, vulnerabilities, and risk management gaps. This empowers them to implement appropriate controls, mitigation strategies, and incident response plans, enhancing overall operational resiliency.
- Regulatory compliance: GRC emphasizes compliance with legal and regulatory requirements.
- Enhanced stakeholder confidence: Incorporating GRC principles into the information security and continuity program demonstrates the organization’s commitment to robust governance, effective risk management, and compliance. This fosters trust among stakeholders, including customers, partners, employees, and regulators. Stakeholders are more likely to have confidence in the organization’s ability to protect sensitive information, maintain resilience, and meet regulatory requirements.
Through balancing risk and reward, cultivating a culture of compliance, enhancing stakeholder confidence, integrating and improving decision-making, and utilizing the NIST CSF as a framework for prevention, correction, and detection in the context of governance, universal outcomes that mitigate risk can be achieved.
Chapter 2 breaks down various international laws and standards, while Chapter 3 focuses on governance oversight and management accountability. Again, given the shift from cybersecurity to cybersecurity risk management, leadership at both the board and the executive levels will assume an even greater role in enhancing an organization’s culture, risk tolerance, and “identifying key management accountabilities.” Utilizing an enterprise risk management approach, which looks at cybersecurity risk across the continuum of the organization and the persons that it serves, whether it’s patients, private clients, or government entities, can provide an effective scaffolding upon which to build with the OCEG Ultimate Guide and other frameworks.
Board oversight, typically conducted by the audit or risk committee, is critical for effective Information Security. While executive management oversight focuses on a more detailed level and occurs more frequently, board oversight provides “strategic oversight.” This should involve regular reviews of 1) plans and budgets, 2) risks and issues, and 3) performance and progress. To aid in this process, OCEG has prepared 20 questions that board members and management can use to evaluate information security (see Appendix B).
Some important strategy questions: When reviewing the security strategy, take a step back and evaluate its coherence. Does it tell a compelling story that makes sense? Does it address a comprehensive range of issues? Is it aligned with other organizational strategies? Is it forward-thinking, incorporating stretch goals and proposing innovating practices?
The initial three Chapters provide the foundation for the rest of the OCEG Ultimate Guide, which is focused on implementation. Success factors include sponsorship and oversight, guiding principles, strategies, roadmaps and plans, approach, resource management, and technology management.
Conclusion
The implementation of any plan requires a purpose and effective communication between the stakeholders and decision makers, which reflects the business value. In today’s environment of data breach class actions and government enforcement actions, being organized, having a comprehensive approach that has adequate technical, administrative, and physical safeguards, which are also relayed in a digestible and meaningful way, can assist an organization in achieving its cybersecurity risk management objectives. NIST and the OCEG Ultimate Guide can play a vital role in this process.
Rachel V. Rose, JD, MBA, advises clients on compliance, transactions, government administrative actions, and litigation involving healthcare, cybersecurity, corporate and securities law, as well as False Claims Act and Dodd-Frank whistleblower cases. She also teaches bioethics at Baylor College of Medicine in Houston. Rachel can be reached through her website, www.rvrose.com.


