The digital transformation has made unprecedented contributions to creating a simple, agile and always available experience in many different industries. APIs are critical components of this digital transformation, which enable web and mobile experiences with the end user as well as new digital business models to arise with partner ecosystems.
APIs allow direct access to data and application functionality (API publisher) enabling the application developer (API consumer) to execute multiple business logic transactions against the organization’s core business assets using common web protocols such as HTTP and JSON. However at the same time this trend introduced a new attack surface – the API breaches – a fast growing attack surface resulting in data theft, impersonation and fraud through digital interfaces.
By 2021, 90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI, up from 40% in 2019 according to Gartner. By 2022, API abuses will move from an infrequent to the most-frequent attack vector, resulting in data breaches for enterprise web applications.
During the past year alone, a number of such attacks have affected the world’s largest enterprises. With that came the realization that we lack necessary measures to secure information at the API level on its digital interfaces.
Digital services are based on software-intensive applications that are constantly updated to preserve today’s competitive market. However, despite of the organization’s quality assurance processes, every software-based service may contain software bugs and backdoors that are often identified by attackers; thus, creating security vulnerabilities that can be exploited to permit a wide range of sophisticated attacks. Each new API represents an additional and potentially unique attack vector into the systems, says Gartner. Because API attacks occur due to software bugs and organization-specific designs of core applications, Gartner claims that protecting web APIs with general purpose application security solutions alone continues to be ineffective.
Here is an example of an API data breach on a challenger bank which is 100% API driven. This attack exhibits sensitive data theft using one of their APIs
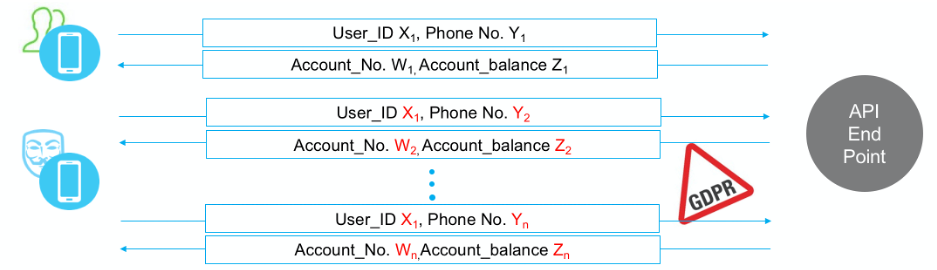
In the normal usage of this service, after successful authentication process, via the web or mobile application, the user receives a list of phone numbers associated with his/her investment account from which he/she could choose to perform an action. In the attack scenario, the attacker bypassed the application and manipulated the API directly using credentials of a legitimate user and random selection of phone numbers. Due to a software bug in their API, the backend application did not validate that the phone number matched the credentials used. As a result, the attacker retrieved sensitive data about other users’ accounts, which resulted in substantial damage to the reputation of the organization and exposure to privacy regulation violations.
In a nutshell, APIs is a growing attack surface that is being exploited by identifying specific flaws in design and software bugs in the implementation of a system. These vulnerabilities can then be used to attack an organizations core assets. These attacks cannot be detected by general purpose application security tools currently available. Therefore, digital organizations that use APIs to expose sensitive data and enable sensitive transactions must consider adding a dedicated and specialized API security layer to protect against API-targeted attacks.
Sharon Mantin is the Founder & CEO of imVision an API Security company. imVision’s solution, API Anomaly Management Platform (AMP) uses Machine Learning and NLP to protect against API specific attacks by automatically learning the API Business logic behavioral patterns and enforcing them.



Pingback: Security first needs to be in every company's DNA - Cyber Protection Magazine