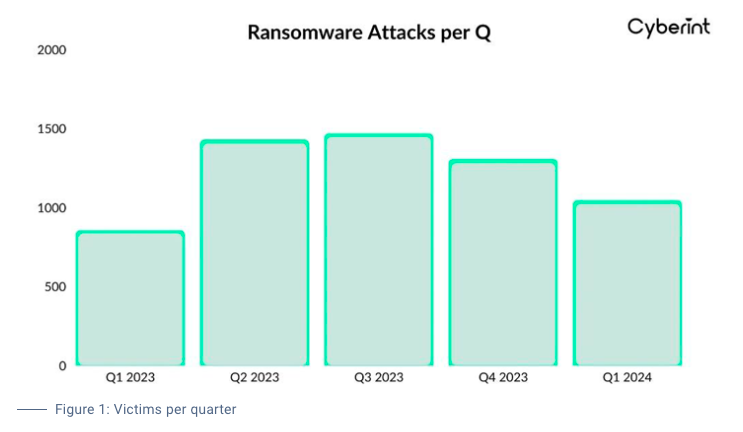
Cybercrime reports flowing out of marketing departments still highlight the danger of ransomware. However, a closer look at the numbers reveals a much different story and poses the question: Have we reached peak ransomware?
Last year, ransomware attacks hit all-time highs with paid ransoms exceeding $1.1 billion and attacks exceeding 5000, according to FBI and Interpol reports. However, looking at midyear reports from Cyberint, SonicWall and Check Point and a dozen others, attacks and ransoms paid have crashed. Still, the crime is not to be discounted, and industry recommendations are to double down on efforts to combat the “scourge”.
There are three reasons why the ransomware industry is hitting a wall.
Law enforcement agencies, working In cooperation, have found the means to identify and shutdown ransomware gang operations around the world.
Potential victims have learned hard lessons regarding the gangs’ willingness and ability to decrypt data, and becoming repeat targets. They are deciding in greater numbers to ignore ransom demands, cutting into revenue streams.
The “honor among thieves” philosophy does not relate to these criminals. Ransomware service providers are stiffing their affiliates, causing a fracturing of the criminal industry into multiple, independent gangs.