Key Guidelines and Simple Takeaways
The steady stream of technology acronyms in cloud security can numb the brain (see our Cybersecurity Cheat Sheets for explanations on some of those acronyms). From CASB to CSPM to CWPP and more, understanding the essence and comparative value of a solution can be daunting. But some are well worth the effort. In this article, we’ll outline Cloud Infrastructure Entitlements Management (CIEM) technology, its easy wins, and the added value it brings to reducing identity access risk.
A brief history of CIEM
It wasn’t just global social upheaval and sweatpants that came into their own during the Covid-19 pandemic. While many of us were adapting to the new normal of working from home, 2020 was a year in which Gartner and others defined new categories of cloud identity-based solutions aimed at reducing entitlements risk to cloud infrastructure and solidifying access governance controls.
The rise in new and automated solutions for detecting, managing, and mitigating identity and access management (IAM) risk caused by cloud entitlements is vital to securing and scaling the infrastructure of a world shifting massively to a cloud-based economy.
According to Deloitte, “a sound IAM strategy is also fundamental for an effective migration to the cloud as it provides for an integrated access solution that is cost-effective, agile, and highly flexible to rapidly enable new authentication methods.” That strategy needs to include effectively securing those cloud identities and their access to the organization’s resources – and in a way manageable to the organization’s security stakeholders.
Many Cybersecurity analysts point to the rise of CIEM technology to meet this strategic need, with businesses increasingly investing in the segment and more CIEM components being incorporated in adjacent solutions to manage cloud-based entitlement risk. CIEM is filling a gap that legacy and other cloud security solutions do not address.
Of the different solutions to emerge in recent years that address IAM in the cloud, Cloud Infrastructure Entitlements Management (CIEM) is proving especially significant in its ability to give the visibility and access control needed to manage cloud access risk across an organization’s multi-cloud infrastructure.
CIEM vs legacy technology
So, we’ve spoken about IAM and its impact on cloud migration, but where exactly does CIEM fit into the equation?
According to Gartner: “Cloud infrastructure entitlement management (CIEM) offerings are specialized identity-centric SaaS solutions focused on managing cloud access risk via administration-time controls for the governance of entitlements in hybrid and multi-cloud IaaS. They typically use analytics, machine learning (ML), and other methods to detect anomalies in account entitlements, like accumulation of privileges, dormant and unnecessary entitlements. CIEM ideally provides remediation and enforcement of least privilege approaches.”
In essence, CIEM tools enable enterprises to more effectively manage their cloud access risks through the governance of entitlements in hybrid and multi-cloud IaaS. What separates CIEM from its individual parts is its ability to blend machine learning (ML) and a range of other methods to detect anomalies in account entitlements in real-time to provide remediation of privileges and policy enforcement all in one process.
How does CIEM reduce identity access risk?
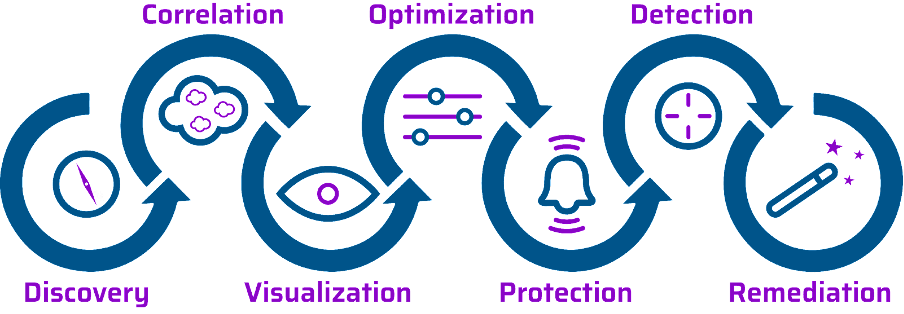
CIEM systems manage and effectively reduce cloud access risk by centralizing a collection of entitlement to enhance visibility and system fluidity.
Account and Entitlement Discovery enables the active discovery and enhanced visibility of all cloud accounts and entitlements seamlessly synchronized with all cloud-based processes.
Entitlement Optimization sets clear limits on access privileges based on the least privilege principle. rather than grant broad system access. Through CIEM optimization, access is limited to only those users/roles based on actual need.
Cross-Cloud Entitlement Correlation standardizes the enforcement of entitlement policies across all clouds. By having consistent policies across all platforms, including for industry standards, organizations can better ensure compliance.
Entitlement Visualization in CIEM brings previously disconnected data points into one, easily correlated, concise, and, in robust solutions, actionable view. Visualization of access to all resources across all clouds allows Security and DevOp teams to better govern and monitor not just access but also the security posture of their cloud environments.
Remediation of access risk and correlation of access rights allows developers to detect threats and respond with alerts or an automated response before the cloud is compromised.
By automating and bringing these identity-first capabilities into one place, in context, CIEM tools can help security, DevOps, or other security stakeholders, including non-technical, more easily understand risks to their cloud infrastructure and their severity. As a result, these professionals are empowered to create a more robust and secure cloud infrastructure in less time and with fewer resources than traditionally required.
More so, by centralizing all data points and entitlement capabilities, identity access can be tracked, altered, and remediated in real-time. Cloud infrastructure, by nature, presents enormous challenges in bringing together the identities, permissions, and systems that are vital for managing access and entitlements for enterprise resources. With CIEM technology, the end-user has the assurance that “the identity of an entity is verified, then granting the correct level of access based on the protected resource, this assured identity, and other context information.”
Additionally, CIEM automation supercharges the process, removing much of the manual effort and integrating policy recommendations in organizational workflows for assessing and implementing entitlement changes according to business processes.
Key guidelines to understanding the value of CIEM
As multi-cloud adoption grows at a precipitous pace and the worldwide cloud market expands to an estimated valuation of 250 billion dollars, the need to optimize cloud entitlement management, minimize the cloud attack surface upon a data breach and protect sensitive data is paramount.
By using CIEM technology, organizations can compartmentalize security gaps, minimize excessive access permissions, and monitor behavioral anomalies across geographic and digital borders.
- Visibility and Automated Risk Analysis is the Name of the Game
The combination of one-part divergent data points, two parts complicated management solutions, and a dash of a disconnected security can often become a sure-fire way to ensure data breaches. With CIEM solutions, security stakeholders can easily look into all multi-cloud identities, user and service, as well as network, data, and workloads, with one clear and cohesive view.
- Simplicity is Key
With 90% of data breaches the result of human error, any process that can mitigate a significant portion of human involvement is essential, and this is especially true when working in the cloud. With CIEM platforms, the complexities of managing and visualizing risk in cloud infrastructure are streamlined to empower IT, admins, to better manage and protect their cloud resources.
- Understanding the Benefits of Cloud First Tools
Legacy systems lack the core functionality and security protection’s part and parcel to IAM solutions. With CIEM systems, a focus on a cloud-centric approach to data and entitlement management is cultivated from square one. By bringing together numerous systems optimized through the cloud, CIEM products enable a leaner, more efficient, and in practice manageable approach to enterprise functionality vs. legacy architecture.
- Managing Risks means Visualizing your Data
You can only be ahead of the risks you know. In the absence of multi-cloud tools that pull together information on all identities and entitlements, security teams struggle to get a complete picture of security gaps and potential vulnerabilities. With the centralization capabilities of CIEM, users can gaze beyond the fog in the cloud to deeply understand, prioritize and mitigate cloud infrastructure access risks in real-time.
Bringing together his diverse professional cyber know-how, intellectual fascination with history and culture, and eclectic academic background focusing on diplomacy and the cultures of Central Asia, Yehudah Sunshine keenly blends his deep understanding of the global tech ecosystem with a nuanced worldview of the underlying socio-economic and political forces which drive policy and impact innovation in the cyber sectors. Yehudah's current work focuses on how to create and enhance marketing strategies and cyber driven thought leadership for odix (www.odi-x.com), an Israel-based cybersecurity start-up. Sunshine has written and researched extensively within cybersecurity, the service sectors, international criminal accountability, Israel's economy, Israeli diplomatic inroads, Israeli innovation and technology, and Chinese economic policy.


