While ransomware is not the most common cybercrime, it is the most profitable. Not only does it pay well, it is fairly easy to set up. A criminal can buy a ransomware toolkit for as little at $100 on some dark web sites and net a profit of more than 2000 percent easily.
It is also relatively easy to keep from becoming a victim of a ransomware attack, but more on that later. First, let’s have a look at the investment and effort needed to kick of a successful ransomware campaign.
The target
Buying a ransomware toolkit is not the beginning. First, you need to identify your victims. That is easier done than said (and no, that was not a typo). All you need are e-mail addresses. A lot of email addresses. Like, hundreds of thousands of email addresses. Luckily, they are easy to find.
A simple Google search for “data breach” will uncover thousands of news stories about data thefts of millions, sometimes billions of e-mail addresses. You can go to the dark web and buy anthem there, but you can do the same thing by searching for “emails” on Instagram. Yes, you can buy drugs, weapons and, important for becoming a ransomware godfather, illegally obtained data. But you can also get it, legally, off of social media accounts. According to RSA, you can even buy stolen credit card numbers off of Instagram.
So let’s say say you have found a database of about 100,000 golf enthusiast you would like to target. Time for step 2.
Tool shopping
The best destination to find ransomware is the dark web. Once there and you will feel like Alice fling down the rabbit hold. There you will find find full service agencies offering to do most of the work for you. Pay a small retainer of as little as $50 and a revenue sharing agreement for a third of the total take and you are off to the races.
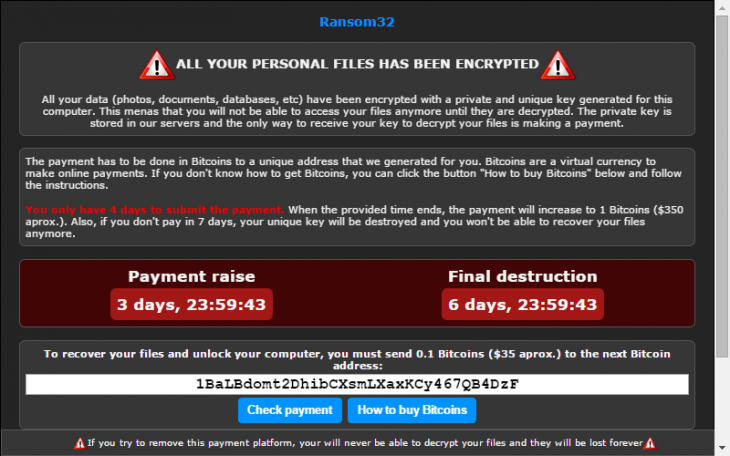
Connecting the dots
Next you’ll craft an e-mail about a grand opening of a new luxury golf resort offering a considerable, but strictly limited, discount for the occasion. The email doesn’t even have to be well written and can contain typos. Put that e-mail into the e-mail distribution program (provided by the full service agency mentioned above).
Unfortunately, these days most e-mail providers offer some kind of ransomware and spam detection, and those have become increasingly effective. So out of the 100,000 e-mail in your database, about 99% bounce, are rejected or go directly to the spam or trash folder. Still, that will leave you with about 1.000 e-mails which actually make it into your victim’s inboxes. Some of your targets might recognize the malicious attempt and not click on your links. That leaves you with, say, 100 victims where you successfully installed the ransomware. All you need is one naive golfer to take the bait in the form of a link. A lot, maybe most, people don’t bother to check where that link goes. They just click it.
Recap
Let’s have a look at the effort you put into this so far. For obtaining the target database, we’ll calculate about one day of research into the darkweb and finding the right database. Another day goes into obtaining the ransomware as such. And then maybe a third day for crafting and sending off the e-mail itself.
Now comes the difficult part: how much should you ask for ransom? You don’t want to ask too much, because in that case the damage for the victims will be high enough for them to report the crime with the police. On the other hand, you don’t want to ask too little, otherwise you will not see any return on your investment. In the golfing example, $100 might be a good amount. People won’t bother going to the police for that, and they are most likely able to afford it, too.
Most importantly: $100 dollars from 100 victims amounts to $10.000. Not bad for just three days of work, is it?
Real life examples
While this might be an overly simplified example of how ransomware works, it’s unfortunately a lot closer to the truth than you might expect. And that includes an entire industry which has evolved to full-service agencies for cyber crimes. In fact, experts estimate that there are only a handful of different ransomware strains out there, created by a few high-profile criminal organizations for an entire army of small cyber crooks for just the purpose we’ve described.
Cyber Protection Magazine’ chief editor helped a pastor extricate himself from such a scam a few years ago only after the scammer had taken $5000 in several payments and bricked the minister’s phone, home computer and church server. So remember, just because your victim pays up, doesn’t mean you have to stop extorting money from them.
Protect yourself
Now to the good news: Protecting yourself is as easy as not clicking on that link in that e-mail. That might seem obvious, but those type of phishing e-mails are increasingly difficult to identify as such. So, whenever you receive an e-mail from someone you don’t know or haven’t explicitly subscribed to, double-check. Usually you’ll easily see something is amiss just by checking whether the e-mail address actually matches the sender or whether the link address matches the actual URL. Doing so will protect you from most ransomware attempts.
The next piece of good news: converting the bitcoin made from criminal activites becomes increasingly difficult, as the case of Heather Morgan and Ilya Lichtenstein recently showed. Arguably, the rise of anonymous crypto currencies facilitated the popularity of ransomware in the first place. The fact that authorities are now catching up and crypto currencies turn out not to be as anonymous as people thought they are sparks hope that the wave of ransomware that has been pestering the world for the past decade might slowly come to an end.
Until then, the best bet is to follow some basic cybersecurity hygiene and, in general, take at least as many precautions online as you would do in the real world.
Patrick Boch has been working in the IT industry since 1999. He has been dealing with the topic of cybersecurity for several years now, with a focus on SAP and ERP security.
In recent years, Patrick Boch has published various books and articles as an expert, especially on the subject of SAP security. With his extensive knowledge and experience in the areas of SAP compliance and security, Patrick Boch has served as product manager for several companies in the IT security sector since 2013. Patrick is Co-Founder and Editor of Cyber Protection Magazine.



