This article is part of our series on Open Source Intelligence (OSINT). Find all articles here.
As I said in my previous article, the dark web is a tiny part of the deep web that we cannot access using regular search engines. The dark web is not one single network; it is composed of many private darknets that collectively form what is known as the dark web. A darknet network is a decentralized peer-to-peer network, some of the darknet networks are relatively large and powered by official organizations or public initiatives, while others are small and run by individuals. The most popular dark networks are: TOR (https://www.torproject.org), I2P (https://geti2p.net), Freenet (https://freenetproject.org/index.html) and Riffle (https://github.com/kwonalbert/riffle).
To access darknet websites, special software is needed, as darknet networks are encrypted and cannot be accessed directly via regular web browsers. For example, to access the TOR network, you should use the TOR browser.
The dark web is famous to host websites that promote illegal products and services (see Figure 1) such as drugs and arms trade, stolen financial and private data, false government documents, child pornography and all sorts of illegal activities can be found there, commercial transactions in this hidden layer occur via cryptocurrencies (mainly Bitcoin). The vast spread of illegal activities should not make us omit the legal side of this layer, for instance, darknet contains many legal websites commonly run by human right activates and journalists that exploit the anonymity of this network to promote their activities and remain anonymous online.
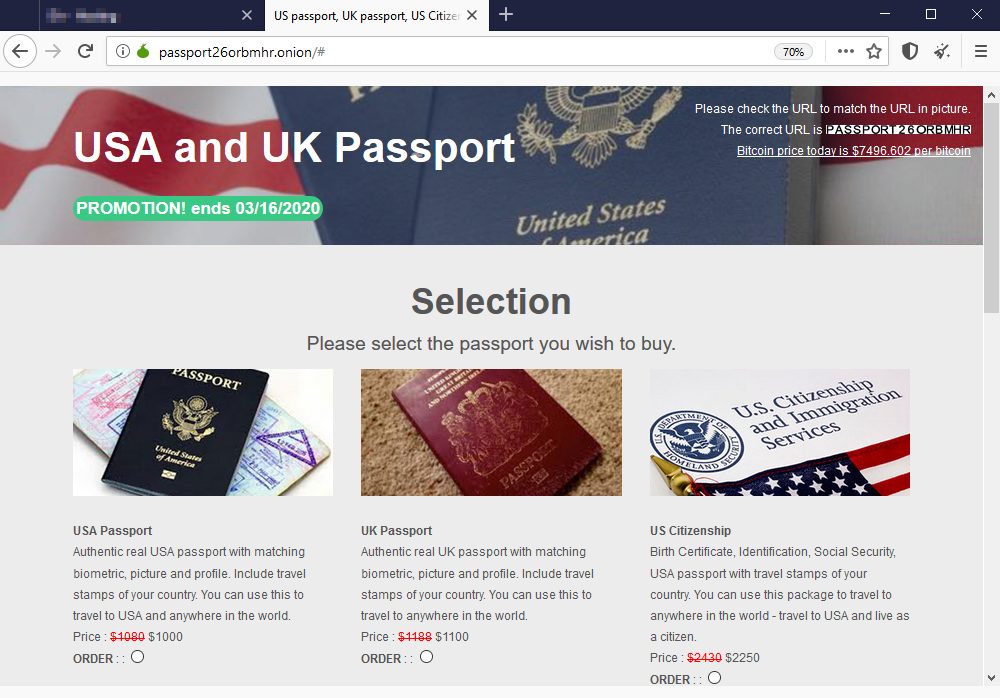
In this article, we will talk about the dark web, how to access and where to start searching it, TOR is the most popular anonymity network exist in the dark web, so it will be the focus of this article.
TOR Network
The TOR anonymity network is free, open-source software, originally developed by the US Navy Research Laboratory (NRL) in the mid-1990s to protect intelligence online communications. Later in 2004, the NRL released the TOR source code under a free license. TOR is now managed by The Tor Project, Inc, a non-profit organization that maintains TOR development.
TOR network is composed of two components:
- The TOR software used to access the TOR network.
- TOR infrastructure, which is simply a set of volunteer computers spread all over the world that route users traffic across the TOR network.
TOR network can be used to anonymize internet user’s online identity when surfing the surface web, in addition to enabling access to TOR anonymous websites (also known as TOR hidden services). To use TOR to browse the surface internet anonymously, all you need to do is to download the TOR browser (https://www.torproject.org/download) and use it -as you do with your regular web browser- to surf online.
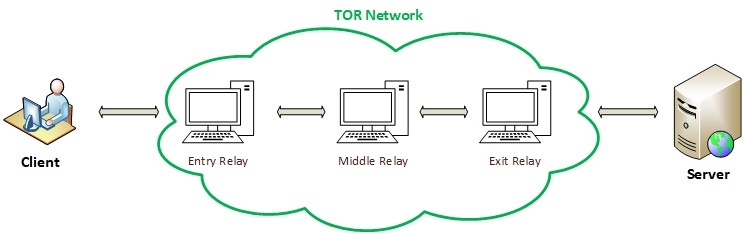
TOR anonymizes internet traffic by bouncing your connection over at least three relays (also known as nodes or routers) before reaching the final destination (see Figure 2). The first relay is the entry relay (also known as the guard relay), it routes your data from the surface web and moves it to the middle relay. TOR uses at least one middle relay for each connection, however, it may use more, the middle relay then shifts your connection to the final one which is the Exit relay (see Figure 3). When surfing the surface web sites using the TOR browser, your real IP address will be concealed and your connection will seem to originate from the TOR Exit relay IP address instead. Using TOR will efficiently hide your identity online and prevent websites from tracking your browsing history. TOR is also considered a valuable tool to circumvent censorships implemented in many countries.
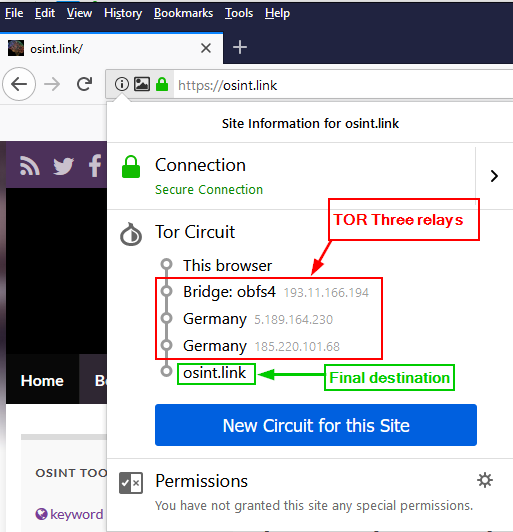
Data going through the TOR network is encrypted, however, when the data leaves the TOR network (at the Exit relay), the data need to be decrypted again to continue its way to the final destination on the surface web. The Exit relay can be misconfigured by a malicious actor to intercept the traffic, so it is advisable to encrypt your sensitive data before sending it via the TOR network.
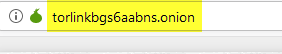
The address of the TOR hidden services -also known as onion services- is composed of a series of random string characters (numbers and letters only) and ending with the .onion extension (pronounced “dot-onion”) (see Figure 4). A TOR hidden service is fully anonymous and allows its owner to use it to promote various activities on the TOR network like anonymous instant messaging and web publishing in addition to sharing files anonymously.
It is a good practice to conceal your entrance to the TOR network, although, using TOR is considered legal in most countries, however, using it may consider somehow suspicious and raise a red flag especially when TOR traffic pass through the government’s firewall. To conceal your TOR usage, use a VPN connection before connecting to the TOR network. TOR also provides a mechanism to hide its usage known as “pluggable transport”. You can find a full guide on how to use TOR pluggable transport at https://2019.www.torproject.org/docs/pluggable-transports.html.en
Searching TOR network
Surfing the TOR network is not easy as surfing the surface web sites, the ephemeral nature of TOR hidden services in addition to the absence of powerful search engines (like Google and Bing) for indexing the TOR darknet, make finding onion sites a difficult task. There are many dedicated TOR search engines and TOR portals that try to simplify finding TOR hidden services by providing a directory of TOR sites. The following are the most popular TOR search engines/directories:
- The Hidden Wiki (http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion)
- Ahmia (http://msydqstlz2kzerdg.onion)
- Torch (http://xmh57jrzrnw6insl.onion)
- TorLinks (http://torlinksge6enmcyyuxjpjkoouw4oorgdgeo7ftnq3zodj7g2zxi3kyd.onion)
- NotEvil (http://hss3uro2hsxfogfq.onion)
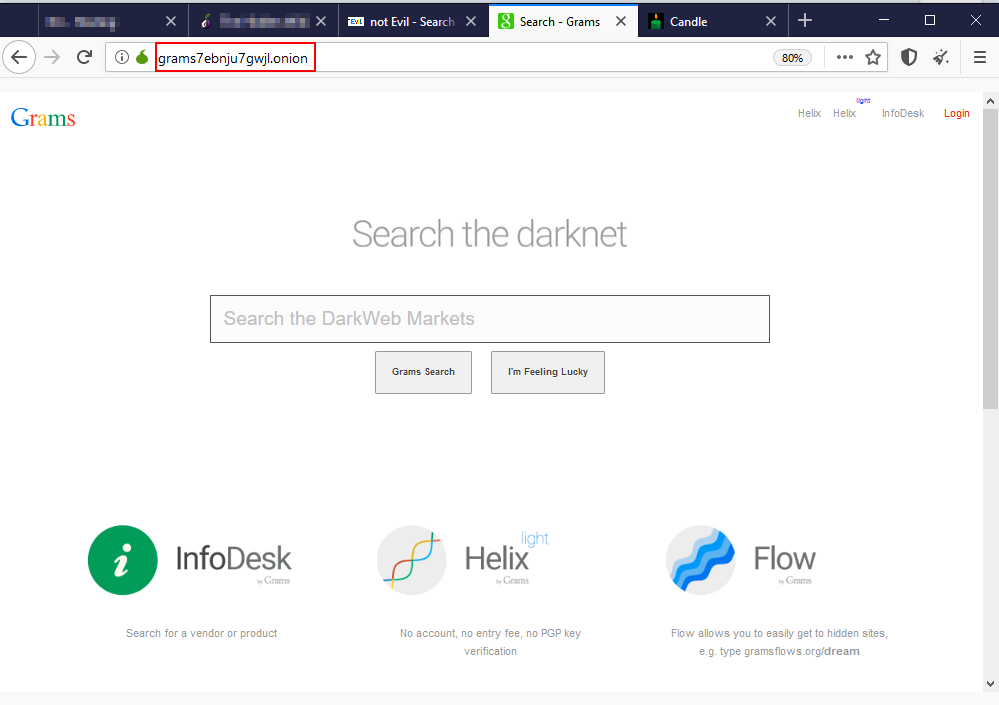
- Grams (http://grams7ebnju7gwjl.onion) (see Figure 5)
- Candle (http://gjobqjj7wyczbqie.onion)
- Tor Onionland (http://3bbaaaccczcbdddz.onion)
Conclusion
The dark web is a term used to name decentralized peer-to-peer anonymous networks, there are many anonymity networks, the most popular one is the TOR network.
TOR is popular among the general public because it allows its users to surf the surface web anonymously, in addition to the regular function of darknets which is hosting anonymous websites.
Dark web networks cannot be searched or indexed using regular search engines like Google and Yahoo, however, for each darknet, you can find many specialized search engines and directory sites that list popular sites hosted in that darknet.
In the next article, we will move to talk about another important field in cybersecurity, Digital Forensics is a field used to investigate digital crimes, it is relatively an emerging field in computer security and its operations intersect many disciplines like online investigations, eDiscovery, and intrusion investigation.
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.


Pingback: How the Dark Web works - Cyber Protection Magazine
Pingback: The Darknet and the Advantages of Using Dark Web Links