Smart security for the data breach era shifted the emphasis from the traditional enterprise focus on ‘North-South’ (‘command and control’ and exfiltration) traffic to internally-oriented ‘East-West’ traffic involving reconnaissance and lateral movement. As security challenges shift to applications and focus on business process-oriented monitoring and protection around APIs, the terms North, South, East and West have new meaning, context and import.
Core business systems are now connected directly to partners, suppliers, customers and other third parties via APIs to give competitive advantage and strategic efficiency and effectiveness in the digital business world. Companies place their trust in the use of these APIs because they are authorized and authenticated, but they have no way to monitor or control what goes on inside them. Now business systems and logic may be fully exposed to legitimate or illegitimate third parties, with little or no way to preempt fraud or misuse.
API Traffic is the new priority
In APIs, East-West refers to a business’s internal traffic and connecting processes to its own internal applications, while North-South APIs connect to third parties and external systems and apps. For today’s CISOs, North-South API traffic is the new priority because most critical business applications are exposed, by design, but lack proper security visibility.
Detection across the enterprise “compass points” is still valuable, but it focuses on trying to find an attacker at work who is focusing the internal enterprise network. These data breach attacks are still a frequent problem, but they pale in comparison to the new types of attacks that threaten a company.
All employees work remotely today, and new business applications are not built in data centers anymore. The new mode of digital business favors cloud infrastructure and applications as well as sharing systems and information with customers, suppliers and partners. APIs are the “new network” that ties transactions and shares data and enables connectivity. At the same time, APIs open the heart of the business to potential theft, abuse or manipulation. Most attackers today therefore focus on these application environments and externally facing APIs as this is their most direct way of making the gain and unfortunately, they are also largely undefended.
Visibility across all APIs
Now, organizations must have visibility of all APIs and monitor the important ones. Existing application security controls don’t address the basic visibility needs. First of all, most organizations know of only a portion of the APIs they use and know far less about how they are used. Second, current API security only addresses known API vulnerabilities and does nothing towards understanding context and assessing behaviors within them. Current API security does not extend to all the APIs unknown to company security teams, nor does it know anything about them. Addressing these two challenges forms a basis of what is needed for API security with the addition of behavioral awareness and assessment.
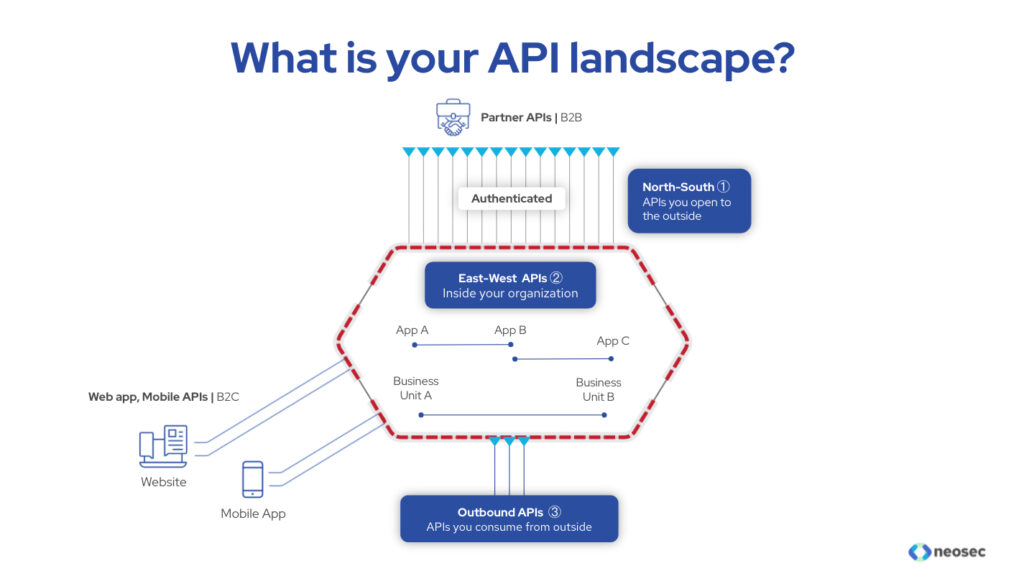
New API security does not resemble network and endpoint security where the challenge is to look for command and control, reconnaissance, lateral movement and exfiltration. APIs are different because they already expose core business functions to the outside – there is no need for classical kill-chain steps. The new imperatives are to identify and catalog all APIs; determine the important ones for business loss, damage, exposure or risk and compliance violations; monitor and assess behaviors; and stop or minimize serious misuse and criminal activity through them.
APIs are not just a stealthy haven for attack activity but the actual means of an attack. Through APIs, external criminals or nation states can steal or damage a business in ways that greatly exceed those from today’s data breaches. Rogue insiders or partners can perpetuate fraud or other activities. Money could be transferred, orders manipulated or diverted and business processes subverted. In the same way that Cambridge Analytica, a legitimate partner of Facebook, took advantage of data accessed via an authorized API, third parties can use APIs to abuse valuable company data, resources and assets to their own benefit. Unauthorized parties can also gain access to APIs to do what is likely far worse.
A new compass for API threats
Most companies today are not equipped to counter these challenges. They must reorient their terminology to a new compass for API threats. Just as adapting the North, South, East and West mentality helped companies better prepare for new style of attacks—which, incidentally, is still not well employed or even non-existent for many organizations—companies must be prepared for the new breed of API attacks that are coming. The stakes are far higher. New solutions and technologies combined with strategies and procedures are emerging to help organizations meet this challenge. Embracing digital business is a necessity, but so is stepping up to a new mode of security to enable and protect it.
Giora is a two-time entrepreneur. Prior to founding Neosec, he was VP Product Management at Palo Alto Networks after his first company, LightCyber, was acquired. He served as an officer in the elite technological unit in the Israel Defense Forces, where he pioneered the development of cyber technologies.



