After decades cybercrime moving faster than the rest of the world, there are indications we may be catching up to cybercriminals. This new trend is due to several, possibly temporary factors.
Cyberattacks are predicted to rise again in 2023 after increasing, by some estimates, by 600 percent in 2022. But a question Cyber Protection Magazine has been asking for almost two years is, how many cyberattacks result in damages and losses to organizations and individuals? Until last week no one offered an answer.
The statistics organization Statista published a chart that showed the number of attacks steadily increasing since 2005 but spiking beginning in 2015 to 2018 which is where the chart stopped tracking. After that, however, other sources, including Flashpoint (https://www.techrepublic.com/article/almost-2000-data-breaches-reported-for-the-first-half-of-2022/), showed the number of records exposed continued to increase dramatically from 471 million in 2018 to 37.2 billion in 2020.

After that, the bottom dropped out. In the first half of 2022, Flashpoint and Statista reported that less than 1.5 billion records were breached. That’s still more than three times than 2018, but it represents a drop in successful data breaches by almost 200 percent in the past three years. Multiple sources confirm that the number of people impacted by the breaches dropped from 2.4 billion to 53.5 million. According to Statista, from 2021 to the first half of 2022 data compromises dropped from an all-time high of 1.862 billion to 817 million in the first half of 2022. To catch up, the second half would require another billion compromises.
Skepticism abounds
Checking in with several respected security experts found a lot of doubt in the numbers, which is understandable. A common trait in the industry is pessimism, but when confronted with corroborating data, the pessimism was combined with guarded surprise.
Gerry Kennedy, CEO of Observatory Holdings, which provides research for the insurance industry, said the problem with the numbers is there is a lack of comprehensive reporting. However, he admitted that if the reported number of breaches is dropping, then unreported breaches should be declining, as well.
To be honest, 817 million breaches and 53.15 million impacted individuals is still a lot, but the trend is going in the right direction. That begs another question, though:
What is causing such a dramatic drop?
In one case, the rapid increase that began in 2015 is explainable. That was the year of the Cambridge Analytica scandal with Facebook revealing the growth of foreign interference in European and US elections. Governments demanded more transparent reporting, so a lot of unreported breaches became public. In 2018 companies began to see insurance premiums spike by as much as 25 percent annually as reporting companies grew.
Investment in cybersecurity budgets is increasing even as companies worldwide are cutting budgets in everything else. Garner recently reported that more than 60 percent of CIOs are planning to spend more on security. Jon Geater, co-founder and chief product officer at RKVST said, “We see companies and governments around the world waking up to the fact that with data-driven and connected operations now the norm, significant risks can enter their business from their supply chain.”
The upside of COVID
Then the pandemic hit in 2019 followed by a rapid transition to working from home. That trend set off alarm bells over remote worker security. Investment in startups for monitoring and securing those workers exploded along with government mandates for digital hygiene. Apparently the warnings work as more people in the digital supply chain adopt multi-factor authentication ((MFA). According to a study by Chubb Personal Rick Services, 80 percent of the respondents said they prefer to use MFA,. That change alone had enormous impact on the strategy for cybercriminals. Cyber awareness blunted the overall success of ransomware and phishing attacks forcing criminals to increase their efforts, sometimes with significant innovation.
Distracted hackers
The Russo-Ukrainian war has been a major distraction to hacker groups that enjoyed protection from state sponsors. In the run-up to the invasion were dire warnings of Russian cyberattacks against Western countries supporting Ukraine. The attacks never came. A form of civil war erupted within the hacker community as they took sides and took away time and resources from other ransomware gangs.
“The Conti Dox was pretty damaging,” said Cyjax CISO Ian Thornton-Trump who also pointed out increased government pressure to unmask and arrest nation-state hackers. “Probably law enforcement has taken unannounced investigation. Cyjax has discovered some intel and we are working with UK/USA Law Enforcement on some of our discoveries. It’s not unlikely EUROPOL may be working on this as well.”
Matt Rosenquist, CISO for eclipz.io, predicted in February that there would be a slowing of ransomware in the first half of the year “with a sharp increase in the back half.” While that sharp increase has yet to materialize, Rosenquist is still predicting an increase.
“I still hold this position, which includes more nation-state ransomware by countries seeking to cause harm/disruption and obtain hard currency.”
Kennedy agreed with Rosenquist. “Expect more attacks if the war winds down. Russia is in deep s___ economically for now. The cyber capital they possess has been pushed back and they need fiat currency fast.”
That being said, the war doesn’t look like it is winding down anytime soon.
Greener pastures in cryptocurrency
The growth of cryptocurrency holdings in the past few years has attracted significant attention from cybercriminals, especially North Korean government actors. North Korea has long funded its nuclear weapons program through the sale of phishing kits and corporate extortion . But a recent CNET story revealed that they’ve turned their attention to raiding crypto wallets and exchanges
The decentralization, lack of regulation, and security weaknesses of cryptocurrency technology make it a verdant field for criminals. The crash of the value of the currency this past year has not deterred them.
“The crypto market decline (most recently due to UST/LUNA issues) does not impact the Ransomware market,” Rosenquist said. “They use cryptocurrency as a payment mechanism. Fluctuations in price are irrelevant, as long as it is still a reliable method of transferring funds. Some attackers choose to keep gains it held in crypto while others sell it off immediately for cash.”
Thornton-Trump agreed. “The crypto market will slowly recover so the funds will appreciate in value but at the same time, the risk of them being caught goes up. It would be interesting to look at the dynamics of this from the threat-actor perspective.”
Investment in cyber pays off
Perhaps more importantly, the increasing investment in cybersecurity services and technology is making a significant impact on the criminals’ return on investment.
A recent attack on a US private equity firm involved using two sophisticated drones, equipped with WiFi tech and a mini laptop, breached the firewalls after using social engineering to capture credentials from a remote worker. The company’s security systems foiled the attack when they saw the employee was already logged in from home. After blocking access a search of the building found the two drones and equipment on the roof. So the attack was unsuccessful and the attackers lost about $20,000 in equipment in the attempt.
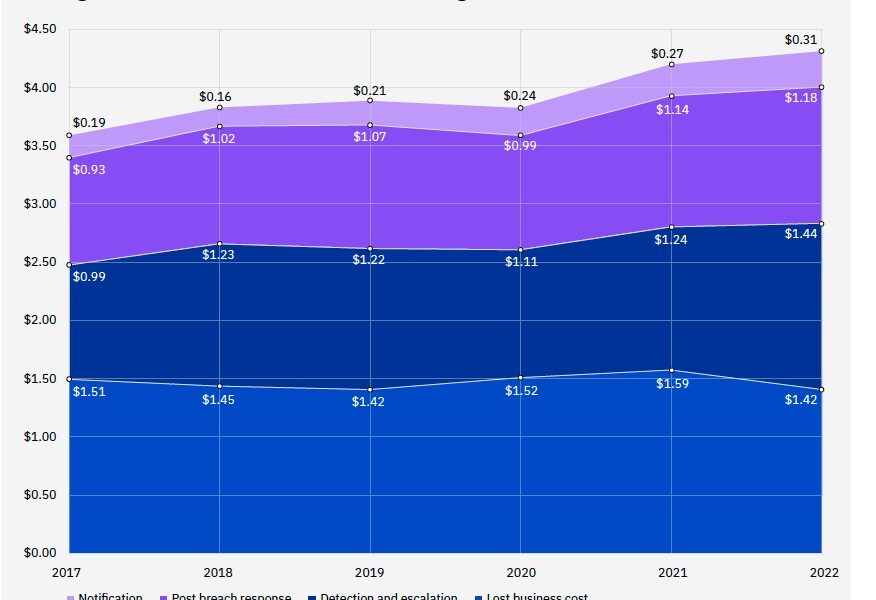
Both the 2022 Verizon Data Breach Investigation Report and the IBM 2022 Data Breach Report indicated a direct correlation between a reduction in business losses to increased investment in notification, response and detection of breaches.
Managed services at the forefront
The dizzying array of tools, technology, and services in cybersecurity has been a hindrance to adoption, along with the lack of skilled cybersecurity services, especially in the SME sector. Corporate leaders just didn’t know where to start. That has led to a dramatic increase in managed service providers. According to Forrester, the sector will reach USD 72.37 Billion at a 13.9% CAGR by 2030. Large corporations and private equity are gobbling up managed service providers. The biggest to date was Google’s acquisition of Mandiant for $5.4 Billion.
Dave Martin, Vice President, Managed Detection and Response at Open Systems said, “Managed service providers have helped many companies combat ransomware and other attacks. Combining 24/7 monitoring, AI automation, and the expertise of experienced security professionals, providers can detect and contain threats early in the cyber kill chain (saving) as much as $8 million annually per company.”
All of this, however, can go away as quickly as it showed up. The Ukraine war could be over by the end of the year. Cryptocurrency regulations are in the offing and some companies and organizations could get complacent. For now, we seem to be seeing the criminal’s tail lights on our way to gaining an upper hand.
Lou Covey is the Chief Editor for Cyber Protection Magazine. In 50 years as a journalist he covered American politics, education, religious history, women’s fashion, music, marketing technology, renewable energy, semiconductors, avionics. He is currently focused on cybersecurity and artificial intelligence. He published a book on renewable energy policy in 2020 and is writing a second one on technology aptitude. He hosts the Crucial Tech podcast.



Pingback: Fraud will dominate 2023 - Cyber Protection Magazine