This is part 4 of our series of articles on OSINT. Find all articles here.
Online Privacy (also known as Internet Privacy) is a general term that refers to a wide array of techniques and technologies used to secure personal & confidential information when going online. Internet privacy has become a hot topic in today’s digital age and it is a growing concern for the general public. Global media channels announce daily news about internet privacy violation incidents that – mostly – come in the form of leaking confidential business or user’s data for malicious purposes.
There is no sign that cybercriminal activity will slow down in the future, on the contrary, all estimates show that it will increase at an exponential rate. For example, Cybersecurity Ventures predicted that cybercrime will cost the world $6 trillion annually by 2021, large portion of this number come as direct or indirect lose caused by internet privacy breaches.
Aside from the concerns of the general public about the security of their personal information and communication online, Online privacy is crucial for IT security professionals and especially OSINT gathers who need a high level of privacy and anonymity when conducting online investigations.
In this article, I will try to give a high-level overview of the subject of online privacy using practical tips, pointing to the many online resources and give technical advice on how to keep your online communications secure and prevent attacks against your computing devices.
Protect your Operating System
The first thing you need to consider when securing your online privacy is to make sure your current OS is secure and does not suffer from any security problems or open holes that can allow outside intruders to gain unauthorized access to your device. The following measures should be followed to secure your OS (we will use Windows as an example in some tips, as it is the most used OS on desktops and laptops worldwide).
- Install reliable antivirus, dedicated antimalware and personal firewall solutions. Comodo offers a free personal firewall solution (https://personalfirewall.comodo.com) and Avast has a free version of its antivirus solution (https://www.avast.com/free-antivirus-download).
- Keep your OS up to date, and do not use discontinued OS (e.g. Windows 7 and XP).
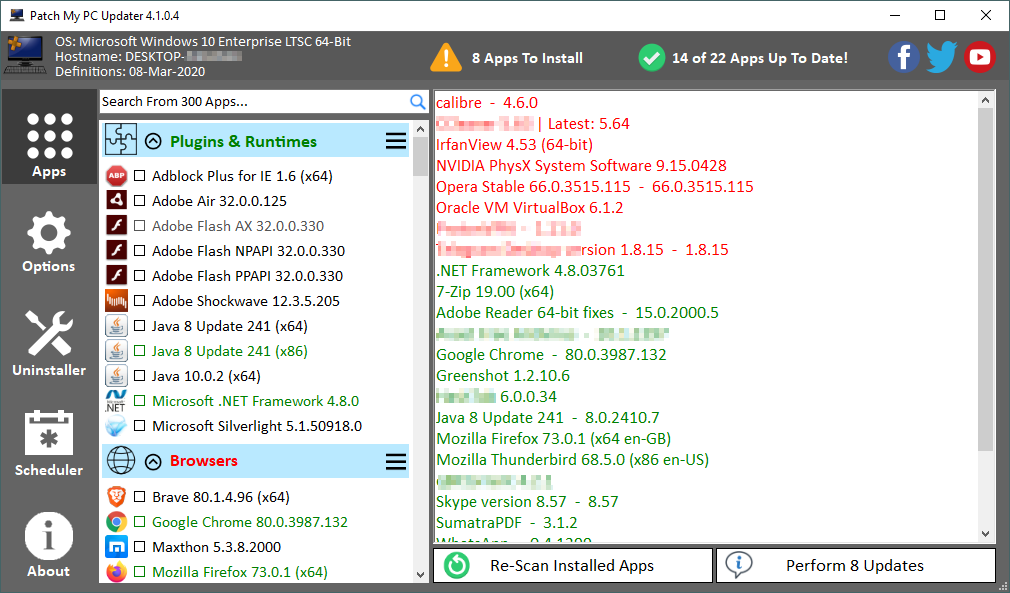
- Keep your installed applications current. You can use a software updater to do this for you, Patch My PC (https://patchmypc.com/home-updater-download) is an example (see Figure 1).
- Using a less-privileged user account, when conducting OSINT searches, there is no need to use an administrator account; instead, use a limited user account for your daily tasks. This will prevent many types of malware from infecting your machine. To set up a limited user account under Windows 10, check this detailed guide (https://www.laptopmag.com/articles/limited-user-accounts-windows-10)
- Secure your OS login with a strong password. Check this mini-guide for creating strong passwords (https://www.darknessgate.com/knowledge-base/perfect-pssw0rd).
- Do not install pirated software, and do not install internet programs unless you trust the program and the website hosting it.
- Disable Remote Desktop Protocol (RDP) to prevent remote access to your machine using this protocol. To disable RDP under Windows 10, follow these steps:
- Press Windows key + X buttons to open the Quick Access menu, click on System
- On the left-hand side, click on Remote Desktop, turn it Off (see Figure 2)
- Use Full Disk Encryption to protect your hard drive. Make sure to encrypt your USB portable devices as well. For Windows users, they can activate the built-in encryption utility “BitLocker” that comes with most modern Windows versions. You can find a full guide on how to use BitLocker: https://www.groovypost.com/howto/use-bitlocker-encryption-windows-10
- Do not run macros in MS office files unless you trust the file’s sender.
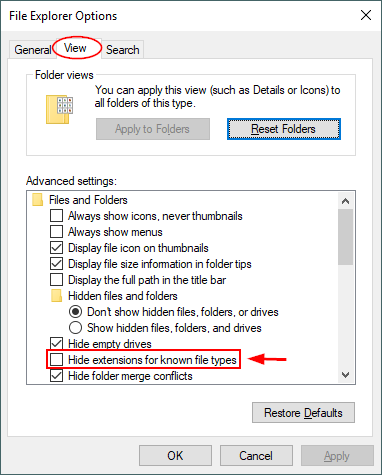
- Show file extensions to recognize potentially malicious files. To view the file extension on Windows 10, go to Control Panel and select File Explorer Options, go to the View tab, and deselect the option Hide extensions for known file types (see Figure 3).
- Cover your laptop camera and microphone, to prevent hackers from recording video/audio if they compromise your device.
Secure Online Browsing
Web browsers are your window to the Web, so you should configure your web browser to use tight privacy options. Restoreprivacy (https://restoreprivacy.com/firefox-privacy) offers a detailed guide for configuring your Firefox browser to become more privacy-oriented. I focus on the Firefox browser because it is still the only true open-source browser, a modified version of Firefox is also used to access the TOR darknet network as we are going to see in the next article.
Many privacy add-ons can help to maintain a user’s privacy when going online, the following are the most popular – and trusted – add-ons for Firefox browser:
- Privacy Badger (https://www.eff.org/privacybadger): Blocks spying ads and invisible trackers.
- HTTPS Everywhere (https://www.eff.org/https-everywhere): Encrypts communications with major web sites, making your browsing more secure.
- NoScript (https://noscript.net): Allows JavaScript, Java, Flash, and other plugins to be executed only by trusted web sites that are selected by the user.
- uBlock Origin (https://addons.mozilla.org/en-US/firefox/addon/ublock-origin): General-purpose ad blocker with custom rules set by the user.
Countermeasures against online tracking techniques
In the previous article, I’ve discussed how online trackers employ various methods to track internet users browsing activities, in this section, I will advise countermeasures to stop this privacy invasion.
Conceal IP address
Internet users can conceal their IP address using two methods:
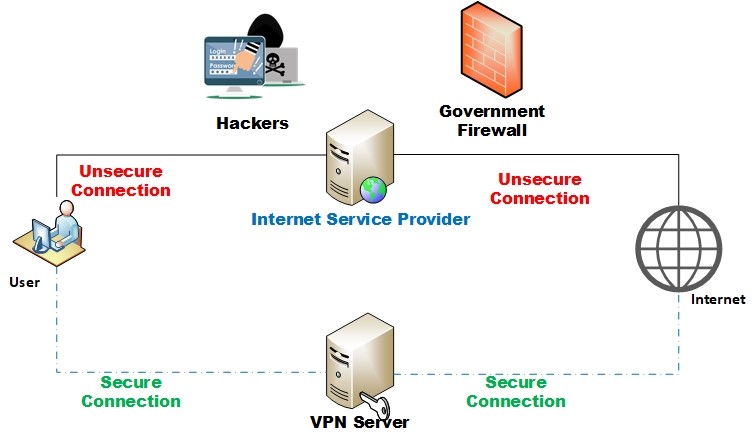
- Using Virtual Private Network (VPN) (see Figure 4): VPN works by establishing a secure encrypted tunnel between the user device and the VPN service, the VPN server will give the users a new IP address making them appear to be connected from other geographical location when surfing the internet. VPN is used widely in the corporate world to secure connections to enterprise intranet when connecting over unsecured networks such as the internet.
- Using anonymity network -such as the TOR browser- to surf the ordinary internet anonymously. This method is more secure than using a VPN service and can guarantee a high level of online anonymity. Accessing darknet will be covered in the next series of articles.
Cookie Tracking
As mentioned before, cookies (especially first-party cookies created by the website you visit directly) are useful to facilitate many useful functions for users when visiting websites, however, third-party cookies are the ones that raise privacy concerns as it can track internet users across multiple websites. So it is better to block third-party cookies and delete web browser cookies upon closing it.
All major web browsers – like Firefox and Chrome – have an Incognito Mode feature, when activated, the web browser will not record user browsing history. To activate this mode under Firefox, open Firefox and click CTRL + SHIFT + P keyboard shortcut, a new browser window appears stating you are in private browsing mode (see Figure 5).
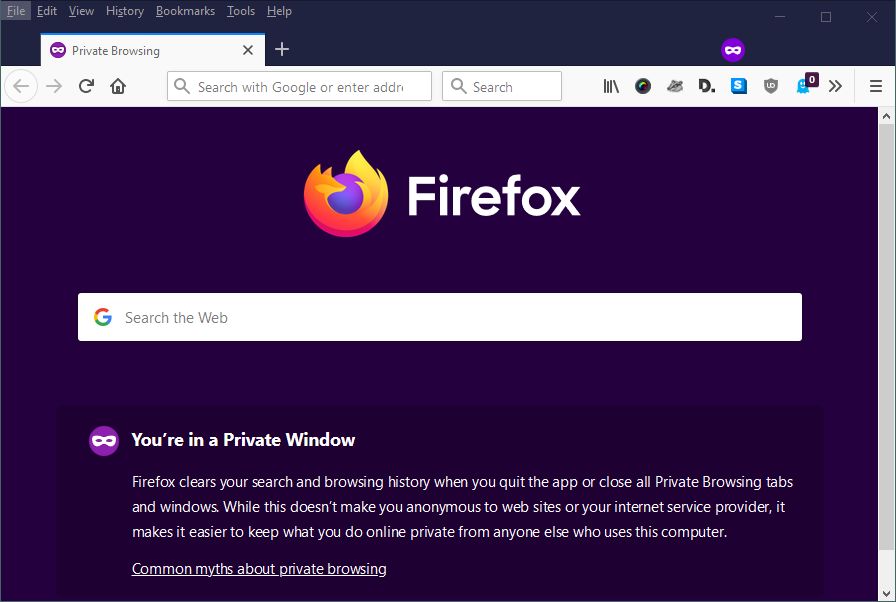
To stop third-party cookies under Firefox, follow these steps:
- Go the Tools menu >> Options
- Select the Privacy & Security panel.
- Under Enhanced Tracking Protection, select the Custom radio button to choose what to block.
- To disable all Third-party cookies, Select the Cookies checkbox and select All third-party cookies (may cause web sites to break) from the drop-down (see Figure 6).

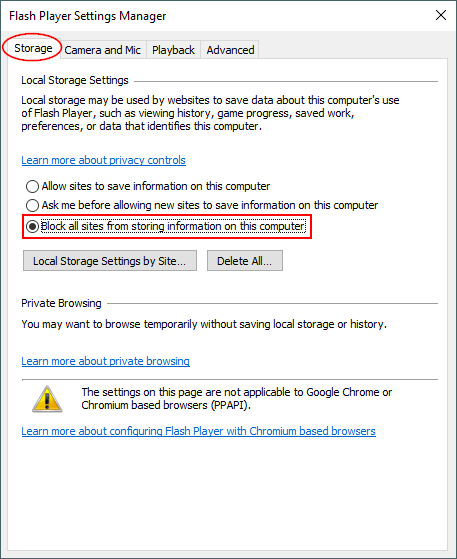
Flash cookies need special arrangement to prevent, as it is stored on user hard drive, to block Flash cookies under Windows, do the following:
Go to Control Panel >> Flash Player and select the option “Block all sites from storing information on this computer” (See Figure 7).
ETag Tracking
To get rid of ETags, you must clear the browser cache content.
Digital Fingerprinting
The only proven method to stop digital fingerprinting is to make your web browser similar to most internet users’ web browsers fingerprint. By doing this, online trackers cannot uniquely distinguish your web browser fingerprint and thus cannot create a profile to record your web browsing activities. Of course, you still need to configure your web browser to block third-party cookies, you also need to use a reliable VPN service to conceal your IP address.
To make your browser fingerprint similar to others, you should use a freshly installed web browser – without installing any add-ons – and run it inside a virtual machine (e.g. Virtual Box https://www.virtualbox.org). Using a virtual machine to run your OS inside it, will also help you conceal your OS fingerprint.
Conclusion
The internet is a hostile environment where different third parties interested in tracking internet user’s activities across the web. In this article, I gave a technical advice on how to stop this invasion and prevent online trackers from profiling your device when going online. In the next two articles, we I will discuss about surface, deep and dark net.
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.



I was just looking for this info for a while. After 6 hours of continuous Googleing, finally I got it in your web site. I wonder what’s the lack of Google strategy that do not rank this type of informative websites in top of the list. Generally the top web sites are full of garbage.
We only launched January 1 and while we have been growing organically quite well it will be a while before we crack into the top Google sites, especially since we don’t pay Google to boost us. 😉
“Thanks designed for sharing such a pleasant thought,
paragraph is fastidious, thats why i have read it entirely”
Pingback: Open Source Intelligence - All you need to know - Cyber Protection Magazine