Ever heard of Paxful Wallet? If you’re one of the 3 million people who use it to buy, sell, and store cryptocurrency that answer is yes. Since that customer base represents less than one percent of the US population, probably not. Unless that is, you are one of the thousands more hit by the Paxful Wallet/Venmo Scam.
This scam typically starts with potential victims receiving a text message or email that says the recipient has made a purchase, through Venmo. The message has official Venmo branding and colors to appear legitimate and will claim there was an unauthorized or suspicious charge made to the recipient’s Venmo account. It will give a link to follow or a phone number to call to verify the purchase. The email version uses the Venmo logo and colors to appear official with a subject line like “Action Needed: Review recent Venmo payment of $99.99.” The body then lists the fake charge details and says to call or click a link regarding unauthorized activity. The phone number, clickable links, and sender contact details provided do not belong to Venmo or its parent company PayPal. Instead, they are spoofed and controlled entirely by scammers running fraudulent operations to steal personal information and money.
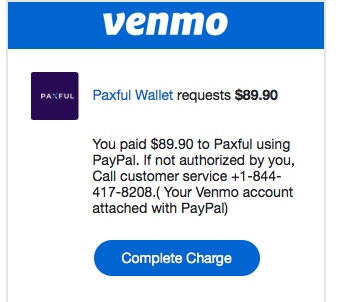
However, it could be even simpler than that. The text this reporter received said. “Paxful Wallet requests $89.90. You paid $89.90 to Paxful… To pay, go to Venmo and complete the request.“
Legitimate companies
Venmo is a peer-to-peer payment app owned by PayPal. Venmo, Paypal, and even Paxful are legitimate companies but their customers are increasingly common targets for scammers because most victims don’t follow basic zero-trust practices. In this reporter’s case, it appears the scammers used our name and email address to set up a fake Paxful account hoping we would approve the payment.
We went to the Venmo app and, sure enough, there was a request to pay Paxful. A request to Paxful for an explanation of how their system allows this kind of fraud is yet to be answered.
A zero-trust approach to this is relatively simple. If you have a Venmo account, go through that app to confirm it was a legitimate contact. In our case, it did come through Venmo and we declined the purchase. Paxful subscribers should check the app or website. Never respond to requests for payment or confirmation through links in emails or texts.
After the fact Defenses
If you do make the mistake of giving remote access to your device, here are steps to take right away:
- Immediately disconnect the device from any WiFi or wired internet to stop the attack.
- Contact Banks and Change Account Passwords with an uncompromised device to access your financial accounts and change any passwords stored on the infiltrated device. Closely monitor bank and credit card statements for signs of unauthorized access. Report any suspicious charges to institutions right away.
- Do a factory reset to wipe them clean of potential malware or spyware. Make sure to change all account passwords after resetting mobile devices and computers. Enable two-factor authentication wherever available as an additional security layer.
- Check and possibly reset home and office systems. Unexplained crashes, slow performance, strange popups, or inability to access your files could indicate a breach.
- File reports of fraud and unauthorized access all institutions tied to accounts potentially caught up in the breach. Provide details on how access was gained by the scammer for accurate tracking and reimbursement claims if money was stolen.
- A credit monitoring or identity theft protection service may act as an early warning system for new fraudulent accounts or transactions opened in your name following a data breach.
But probably the BEST way to defend against this is to limit the use of the services, if not at all.
Lou Covey is the Chief Editor for Cyber Protection Magazine. In 50 years as a journalist he covered American politics, education, religious history, women’s fashion, music, marketing technology, renewable energy, semiconductors, avionics. He is currently focused on cybersecurity and artificial intelligence. He published a book on renewable energy policy in 2020 and is writing a second one on technology aptitude. He hosts the Crucial Tech podcast.