This article is part of our series on Open Source Intelligence (OSINT). You can find all articles here.
The proliferation of the Internet has intensified the number of people who are using social media sites to interact with others and share personal information. This has created a wealth of personal information about almost anyone on earth that is easily and publicly accessible.
Internet is designed as a public network; this makes anything published online readily available to anyone who has a computer with an internet connection. Although social networking sites allow a user to post information as private, the majority of users are still sharing their social activities as public, making such data freely and legally accessible and considered a part of OSINT sources.
Traditional digital forensics methodologies are concerned about acquiring digital evidence from physical computing devices, however, with the increased number of social networking users, information available on social platforms and other public online databases should be exploited in any digital forensic investigation that requires using online public sources to obtain information.
In this article, I will examine using OSINT tools and techniques as a digital forensic investigative tool, focusing on harvesting data about individuals.
Use OSINT to gather intelligence about individuals
We can search for people using either their full name, email address, phone number or address. There are many specialized people data collection websites that offer such service, the following are some popular people search engines:
- Spokeo (https://www.spokeo.com)
- Truepeoplesearch (https://www.truepeoplesearch.com)
- Truthfinder (https://www.truthfinder.com)
- 411 (https://www.411.com)
I will experiment searching for someone using his full name using Spokeo.com (see Figure 1) and then by using his email address.
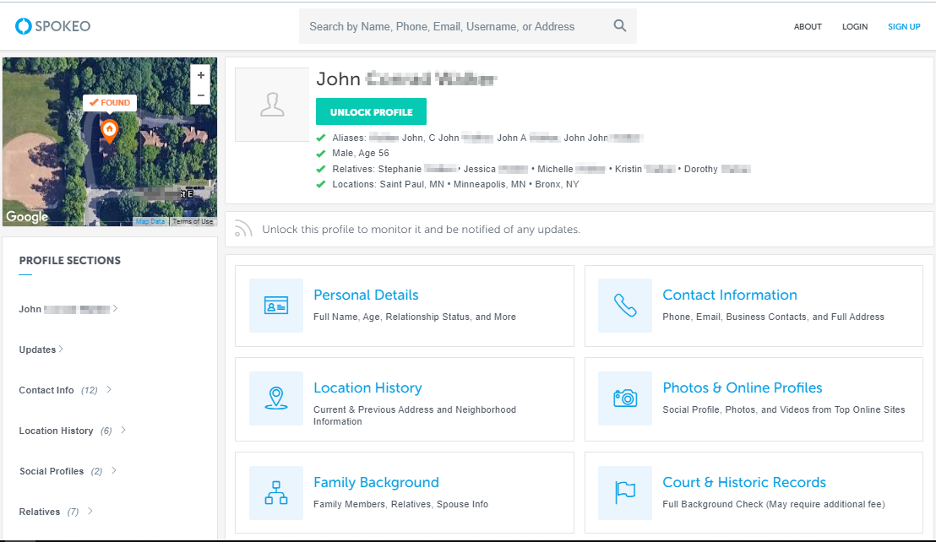
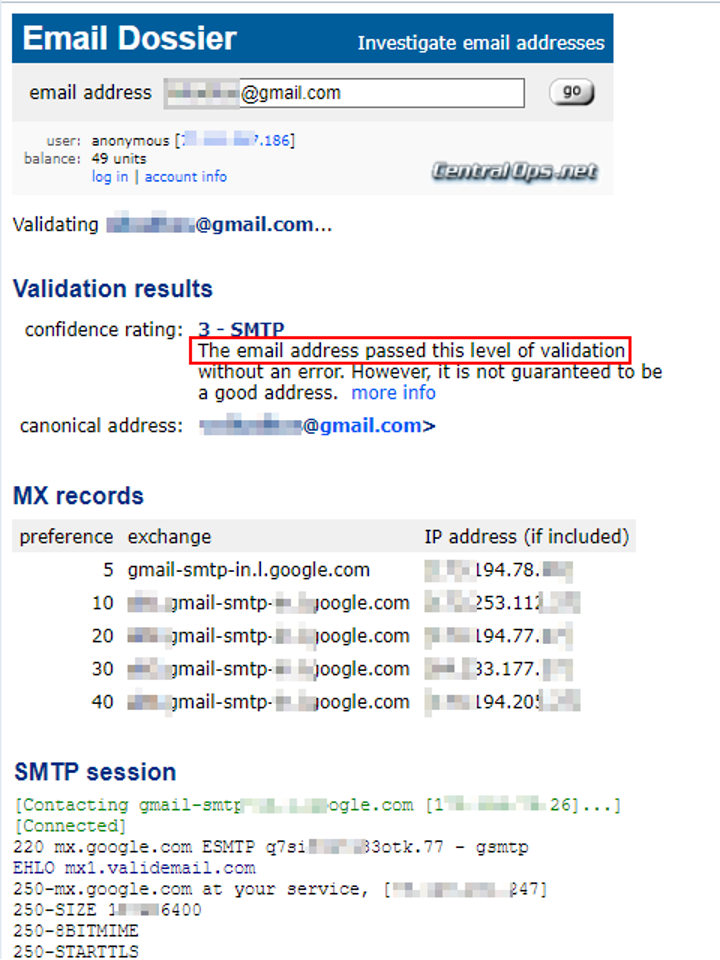
To look up someone using his email address, we can use hunter.io (see Figure 3), however, before start searching by email, we should check whether the target email address is valid or not. I will use a free email verification service, Email Dossier (https://centralops.net/co/EmailDossier.aspx) (see Figure 2).
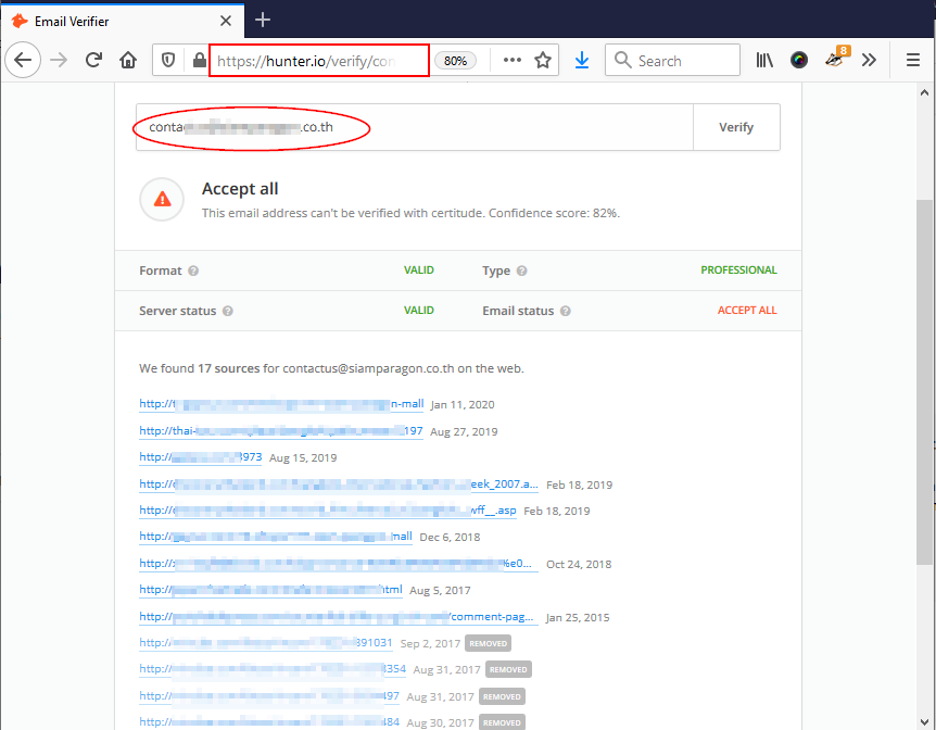
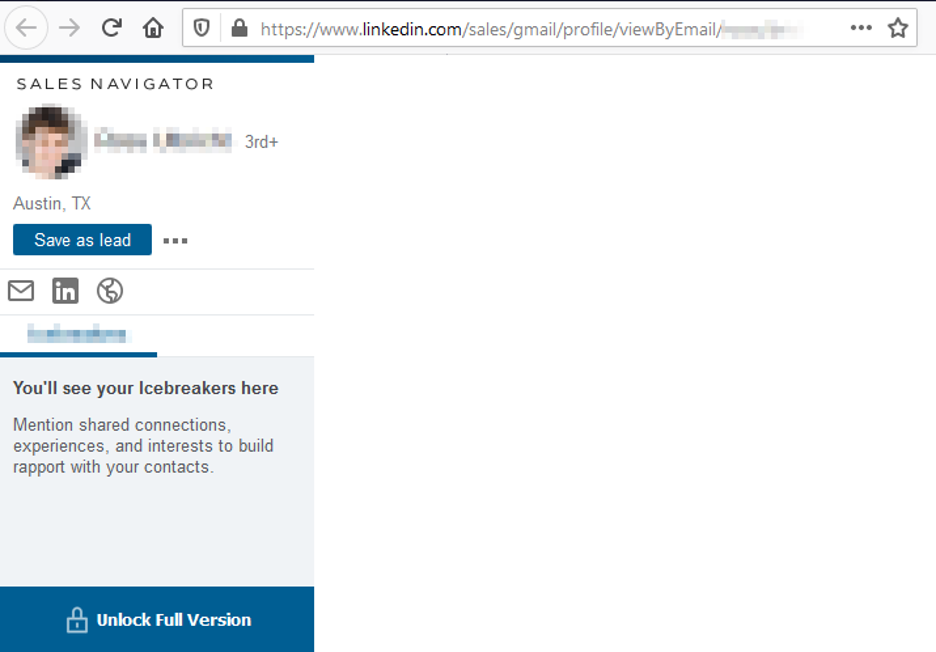
To look up the target on LinkedIn using his/her email address (you should sign to your LI account first to view the result), replace [email protected] with your target email address in the following URL https://www.linkedin.com/sales/gmail/profile/viewByEmail/[email protected]
If the target was using that email address for his LI account and the privacy settings of the target profile are set to allow public search by email, you will see the target profile URL (see Figure 4).
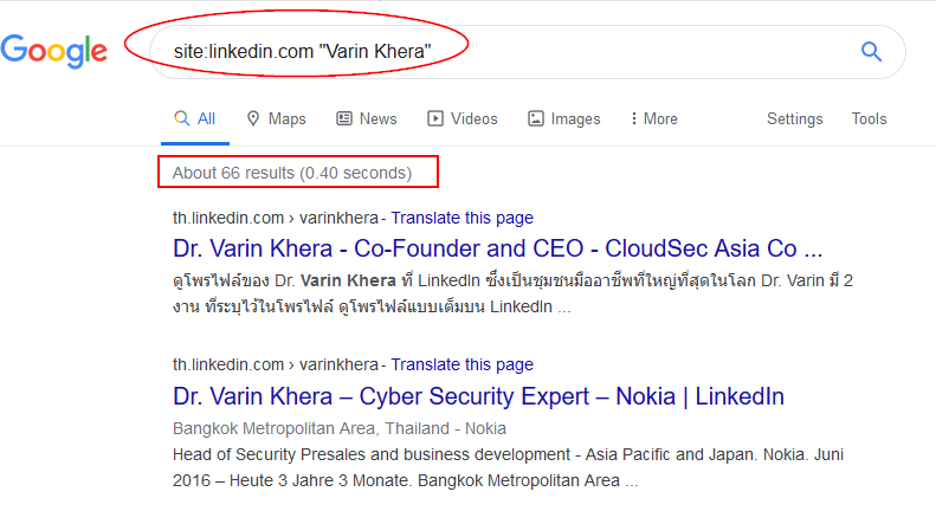
If you have the full name of someone and want to see what information is available about him/her on LI (or any other site), use the following Google Dork (see Figure 5):
Now that you know target LI, you can get his/her photo LI profile photo (if the target included a profile photo) and conduct a reverse image search. Reverse image search engines work by searching the web using a picture rather than using keywords (see Figure 6). The following are some popular reverse image search engines:
- Yandex (https://yandex.com/images)
- Google reverse search (https://www.google.com/imghp)
- Tineye (https://tineye.com)
Investigating social networking sites
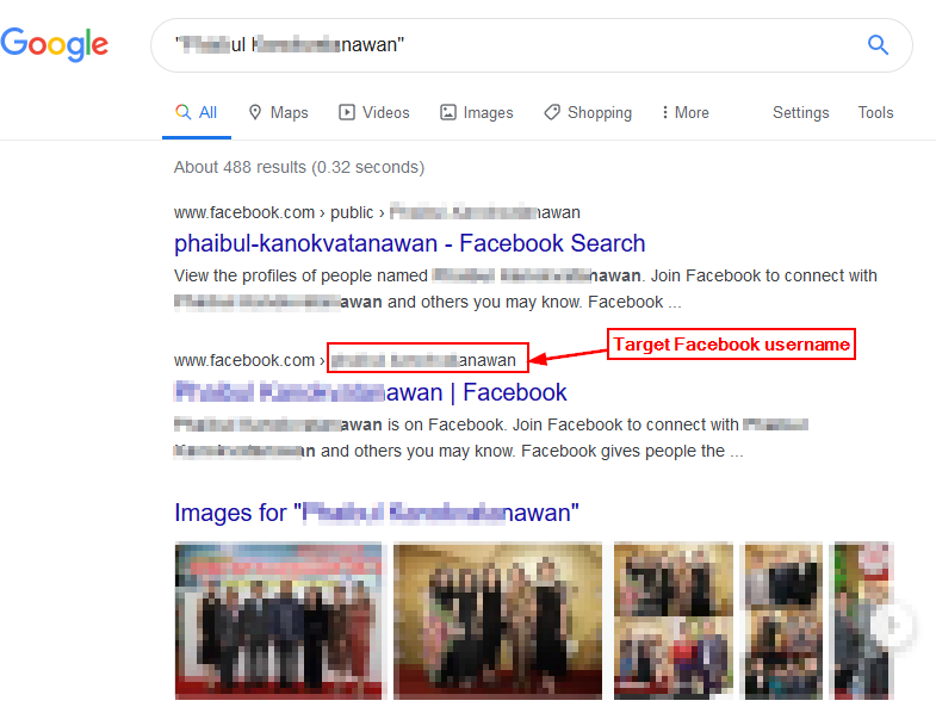
Finding social networking profiles of the target is a great start, by examining the individual’s social media activities, we can obtain a lot of useful information about the target work, friends, online habits, places previously visited, political and religious opinions and much more. All social media platforms such as Facebook and Twitter have a search function where you can search for target name, and examine his/her public posts for interesting facts. For this experiment, I will use Google to locate one of my target social media profile usernames (e.g. Facebook, LinkedIn, Instagram, Twitter) and after then, try to see if the target has used the same username on other places (see Figure 6).
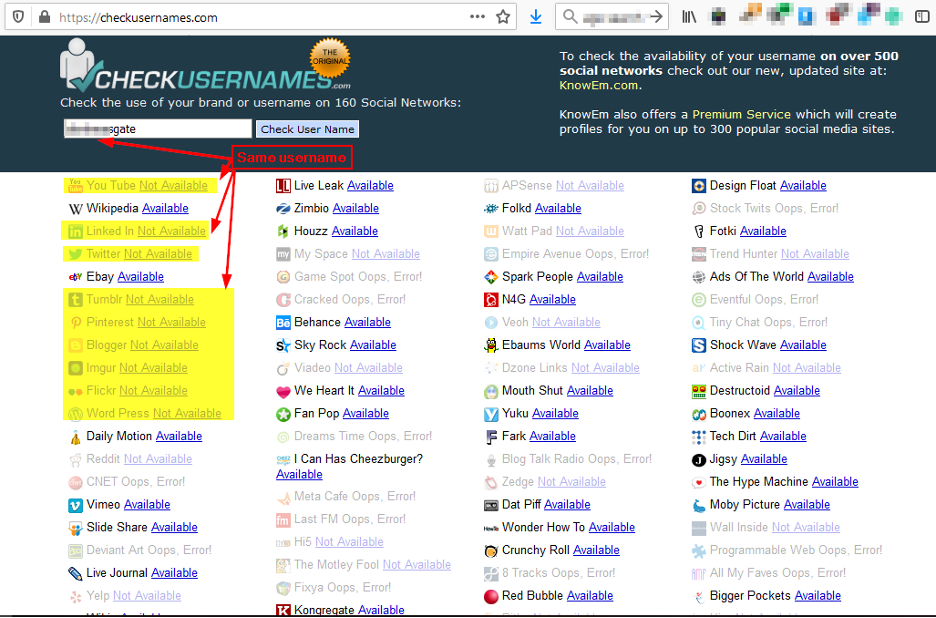
Now that I have my target Facebook username, I can use an online service to see where else this username is used as most people prefer to use the same username on multiple social media services. The following websites, search for similar usernames across scores of social media platforms:
- Namechk (https://namechk.com)
- Checkusernames (https://checkusernames.com) (see Figure 7)
- Usersearch (https://www.usersearch.org)
Investigating digital file’s metadata
While searching for someone, you may find media files (images, audio or video) related to the target scattered on different sites. If the target has some academic background or work in a company where he/she is responsible for posting some types of files online (e.g. Company promotional brochures or job vacancies requirement files), you can also examine these electronic files metadata to obtain useful information.
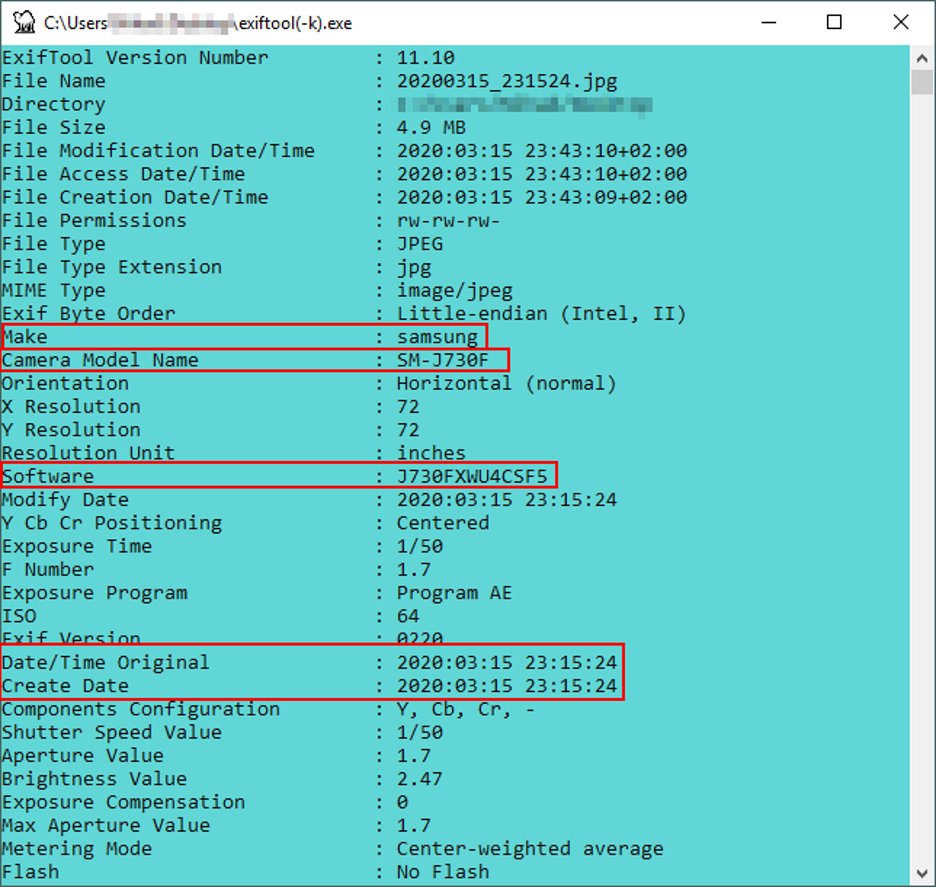
Let us experiment examining a photo metadata for information, I will use the ExifTool from Phil Harvey (https://exiftool.org), to use this tool, just drag the picture you want to extract its metadata above the program icon and you are ready. Figure 8 shows the amount of metadata information that can be extracted from a JPG file.
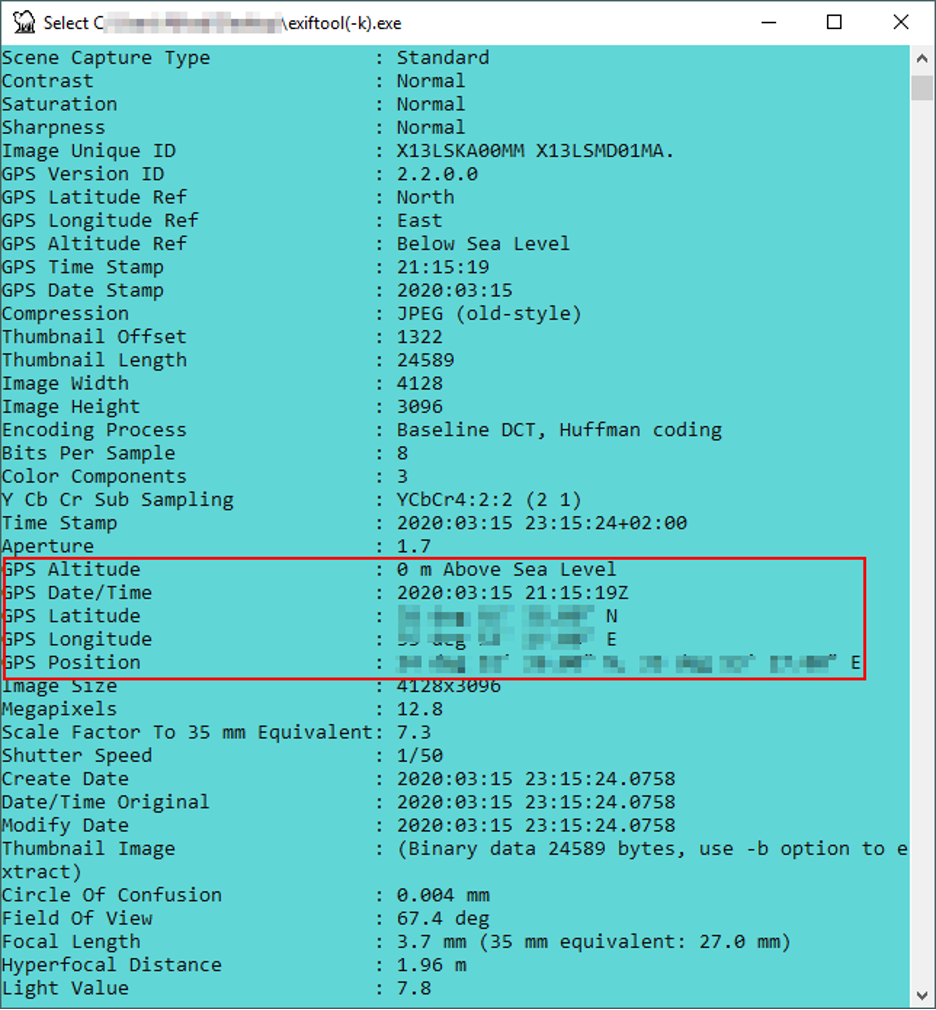
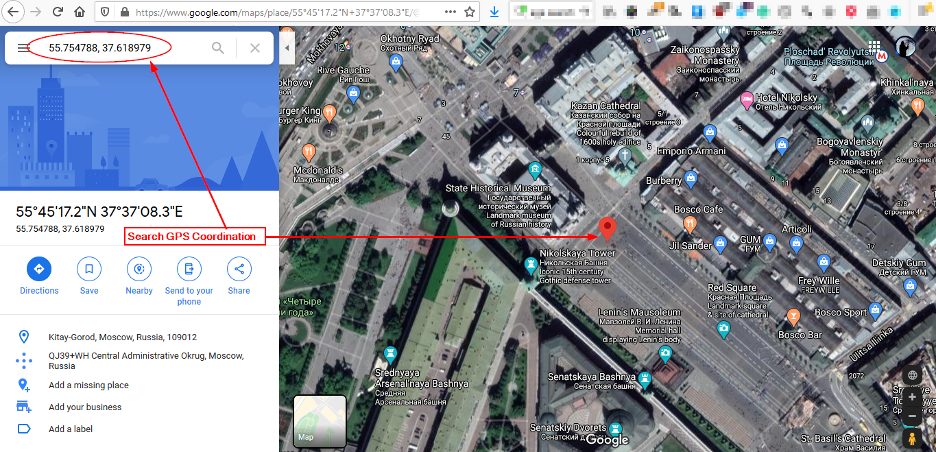
Now that we have the GPS coordination’s extracted from the image above, we can use Google Maps (https://www.google.com/maps) to find the exact geographical location where this photo was taken (see Figure 9).
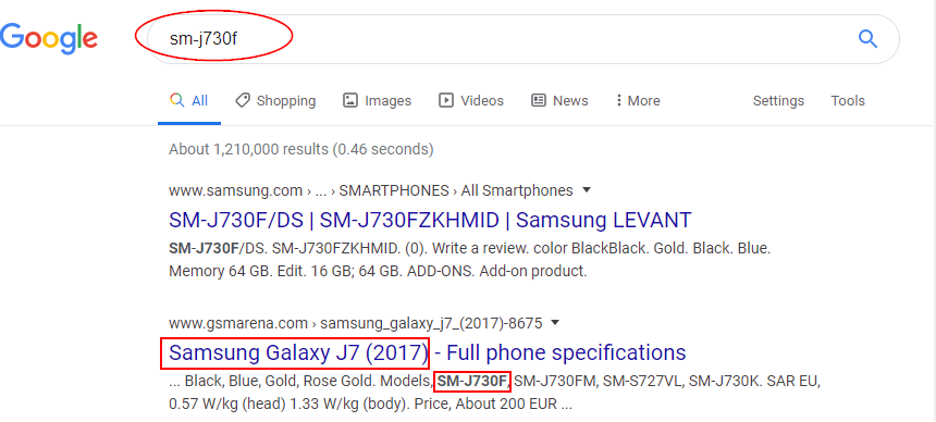
We can also search for the Camera model using Google (see Figure 10)
Searching for leaked credentials on the darknet
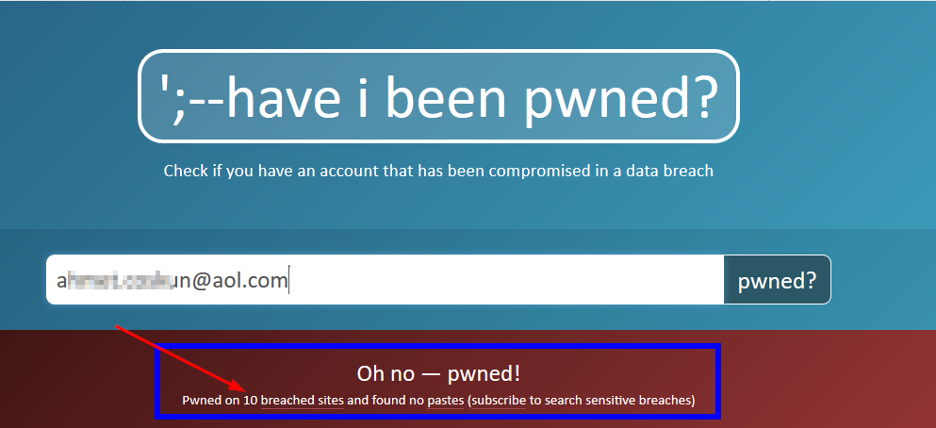
Now that we have the target email address and we are sure it is valid and working, we can search for breached accounts with associated target email. For instance, there are many online repositories that list leaked credentials from breached websites. For this experiment, I will use have i been pwned? (https://haveibeenpwned.com) (see Figure 11).
For each breached website found, have i been pwned? will list detailed information about each breach (see Figure 12).

Now, I have many options to find the credentials associated with each breached account, for instance, I will dive into the darknet and search to see if I can find something about the target email address.
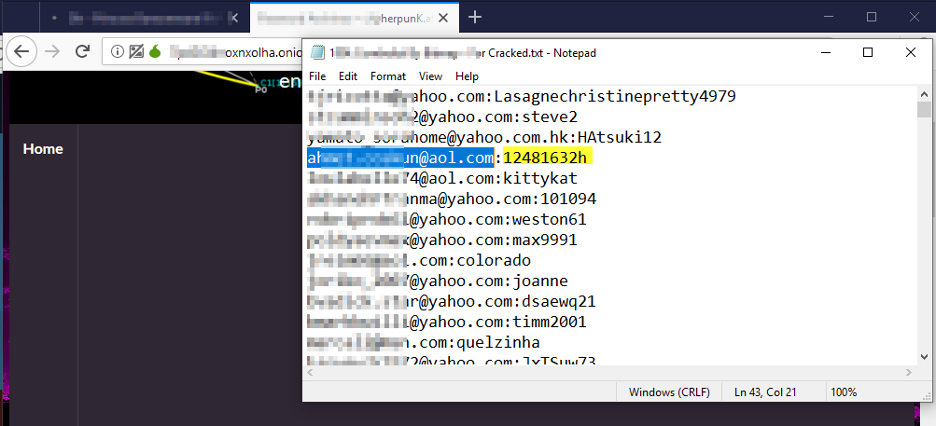
Launch TOR browser, and begin your search, I was lucky to find this file that lists the associated password of one of the target email breached accounts (see Figure 13).
Conclusion
OSINT techniques can be used to harvest different kinds of information about any entity (whether it is an enterprise or individual) online to support our digital forensics investigation. In this article, I tried to give practical scenarios on how we can exploit public data sources through the use of different OSINT techniques to obtain useful intelligence about our targets.
Dr. Khera is a veteran cybersecurity executive with more than two decades worth of experience working with information security technology, models and processes. He is currently the Chief Strategy of ITSEC Group and the Co-founder and CEO of ITSEC (Thailand). ITSEC is an international information security firm offering a wide range of high-quality information security services and solutions with operation in Indonesia, Malaysia, Philippines, Singapore, Thailand and Dubai.
Previously the head of cyber security Presales for NOKIA, Dr. Khera has worked with every major telecom provider and government in the APAC region to design and deliver security solutions to a constantly evolving cybersecurity threat landscape.
Dr. Khera holds a Doctor of Information Technology (DIT) from Murdoch University, a Postgraduate Certificate in Network Computing from Monash University and a Certificate of Executive Leadership from Cornell University.
Dr. Khera was one of the first professionals to be awarded the prestigious Asia Pacific Information Security Leadership Awards (ISLA) from ISC2 a world-leading information security certification body under the category of distinguished IT Security Practitioner for APAC.



Pingback: How to Use OSINT Tools and Techniques to Support Digital Forensics Investigations - ArchIntel™
Pingback: Open Source Intelligence - All you need to know - Cyber Protection Magazine