
Quantum Cryptography

Is Backup Still Relevant?
The end of March marks World Backup Day, a day traditionally designed to raise awareness of the importance of backup and encourage best practices. However, in 2024… Is backup still relevant?

How the cybersecurity industry has changed with 20 years of Cybersecurity Awareness Month
Every year for the past twenty, October has reminded us about the importance of digital security and empowered everyone to protect their data from digital forms of crime. Towards the end of Cybersecurity Awareness Month we’ll take a look back – and ahead.

7 Most Dangerous Cybersecurity Threats
In the ever-evolving landscape of technology, each year brings a new set of cybersecurity threats that can put your digital life and sensitive information at risk. As you navigate the digital world, staying informed about the latest dangers lurking in the shadows is crucial.

Call for Content: We’re going offline – again.
We have partnered with it-sa365, a printed issue of Cyber Protection Magazine will be distributed there. And you can be part of it!

Quantum Computing: the next big thing or science fiction?
It seems like quantum computing is the core fusion of the tech industry: it’s always only a few years away – but is it? We interviewed Matt Campagna, Chairman of ETSI’s Quantum Safe Cryptography group.

Ransomware Recovery: Why a multi-layered approach should be a priority
In order to strengthen cybersecurity and reduce business risk, organisations must employ a multi-layered data protection approach to ensure resiliency and recoverability at any point of the data lifecycle.

Fraud will dominate 2023
It’s that time of year for making predictions for the coming year and the team at Cyber Protection Magazine put out the call in early November with two requirements. Predictions could not be self-serving and could not be obvious, like

Black Friday – Deals, Hacks and Scams Aplenty
With Black Friday and Cyber Monday fast approaching, this weekend is gearing up to be the biggest e-commerce event of the year. But, with this popularity comes the increased interest of cybercrimminals who seek to take advantage of retail’s busiest time of the year.

Cybersecurity Awareness Month – How can Organisations Protect Themselves from Cyber Threats?
As the Western world continues to deal with the fallout of the COVID-19 pandemic, the war in Ukraine, and resultant economic headwinds, cybersecurity is more important than ever. Here is part 4 of our expert commentaries for Cybersecurity Awareness Month.

Insider Threats in Your Digital Workplace
September marks the fourth annual National Insider Threat Awareness Month. So, what can organisations do to prevent a cybersecurity incident?

Defanging the Horror of Quantum Computing
Quantum computing is often in the news, mostly about how it’s going to destroy the world as nation-states bust the hardest encryptions around so they can steal national and corporate secrets. However, there are no quantum computers available today that
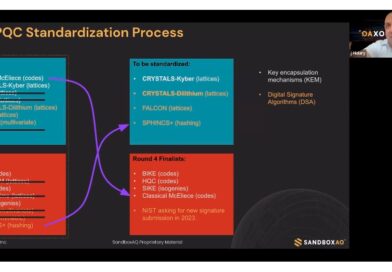
Demystifying Quantum Cryptography
The NIST announcements about 4 algorithm standards to protect against quantum computing hacks had marketing departments go into overdrive. We decided it’s time to start demystifying quantum cryptography.

How to protect personal data with technology
Personal identity information (PII) is more vulnerable than ever, so securing it becomes more important. CPM gives an overview of current and future solutions.

Arqit Suit Pulls Back the Curtain on Quantum
The Arqit shareholder fraud lawsuit is pulling back the curtain on the Quantum computing industry. Before it’s over we may see how much is FUD, snake oil and legitimate.

Lawsuit Pulls Back Curtain on Quantum Crypto Industry
The benefits of quantum computing are a bit hazy, but the danger of the technology is significant. Nation-states are pushing hard to develop quantum computers primarily to break the strongest encryption codes available. That makes governments, infrastructure organizations and corporate

Not if, but when: Why it’s time to prepare for the quantum threat
In recent months, the drumbeat of warnings about the quantum security threat has reached an alarming crescendo. For a reason: the encryption standards we rely on today are at serious and imminent risk.

Predictions Finale: Legislation, standards drive chip security in 2022.
Finishing up our series on 2022 predictions we went to some of the people we’ve talked to in the past year to get their views on what will influence chip security for the positive in 2022.

Make semiconductors secure… or else
Last week, the 58th Design Automation Conference (DAC) in San Francisco dropped a few hints that the semiconductor industry will finally consider making chips secure before manufacturing. However, not without kicking, screaming and complaining.

Quantum computing is not really here, yet. But companies are getting ready for it
Quantum computing is one of those technologies that causes hyperbole, confusion, and concern. A lot of the discussion is not much more than wishful thinking or uninformed fear. For most people, it will not affect them in their lifetime. That’s not to say it isn’t something to completely ignore.
We talked to Alan Grau, VP of business development for the startup company PQShield in this week’s episode of Crucial Tech to get an overview of where we are in quantum security and what their company has to offer.

