
Phishing grows but can be blunted
Phishing attacks are on the rise again with the help of sophisticated generative-AI tools. However, new defenses and increased wariness among potential victims are blunting phishing’s potential for widespread harm.
For the uninitiated, phishing is a foundational practice for all cybercrime. For the most part, it is a scatter-gun methodology, sending out as many emails, texts, social media posts, and even phone calls as possible to get victims to give up personal information or access sensitive files. There are billions of phishing attacks going on around the world every year. According to FBI reports, the latest report shows losses in 2022 were more than $10 billion. The totals go up every year.
Phishing on the rise
Huntress recently issued a comprehensive report on the state of cybercrime that showed an alarming increase in the number of attacks in 2024 using no less than 285 different forms of attack. Modern attack methodologies go far beyond just sending out massive amounts of emails. They can also include an “urgent” voicemail or text, urging the victim to immediately click on the link of an email; infiltrating reply chains; QR codes instead of links, and signature impersonations.
One new phishing kit is Astaroth, which was revealed in January by SlashNext, a cloud email security provider. Primarily marketing on the Telegram messaging platform, the kit sells for $2000 and includes free trials.

Pig butchering: Proving the Luddites right
Pig-butchering may be proving the Luddites were right. The social-engineering scam bypassed ransomware as the most profitable cybercrime approximately two years ago. After government regulations and law enforcement took a big bite out of returns for ransomware this past year, public-private partnerships are taking aim at the new champ.
TL;DR
* Pig butchering eclipses losses from ransomware
* Top targets are tech savvy people under 50
* Human error trumps cyber awareness
* Public/private partnerships making inroads at dismantling scam operations
* Tips to avoid scams
* Podcast with Arkose CEO
Between 2020 and 20023, scammers reaped more than $75 billion from victims around the world. Approximately 90 percent of the losses came from of purchasing fraudulent cryptocurrency, according to the US Treasury Department’s, Financial Crimes Enforcement Center. In comparison, ransomware attacks in that same period harvested $20 billion worldwide in ransoms and cost approximately another $20 billion in recovery costs.

How Breach and Attack Simulation (BAS) Enhances Robust Cybersecurity Practices
Traditional methods of safeguarding information assets have become insufficient in today’s world of advanced cybercrime strategies. A more proactive approach is needed. This article explains the concept of breach and attack simulation (BAS).

The Evolution of Ransomware: From Simple Scams to Advanced Cybercrime Strategies
Ransomware vulnerability is typically exacerbated by immature security programs, leaving organizations susceptible to a variety of infiltration tactics. Additionally, a lack of security culture within companies increases susceptibility to ransomware attacks.
Free Membership Required
You must be a Free member to access this content.

The Importance of Cybersecurity for Small Business
Small businesses face a myriad of cybersecurity threats, with ransomware and malware being the most prevalent. The consequences of such breaches can be profound and multifaceted, affecting various aspects of the business.
Free Membership Required
You must be a Free member to access this content.

Cyberattack repercussions: dealing with the people perspective
Today’s organisations are all too aware of the potential financial, operational, and reputational costs posed by cybersecurity threats and the importance of fortifying defences and boosting their cyber resilience capabilities. And with good reason
Free Membership Required
You must be a Free member to access this content.
Do corporations really care about your security?
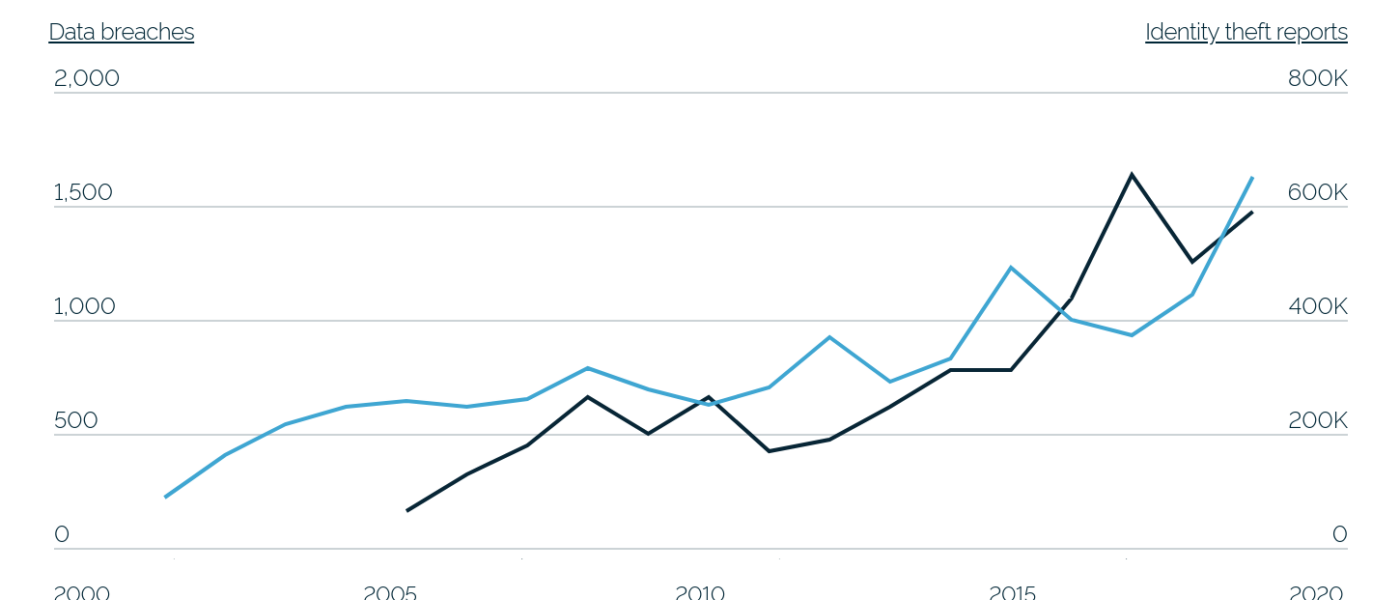
“Your security is important to us,” is a common phrase on corporate websites and emails, usually after some data breach that affects customers. To prove that statement, corporations invest billions of dollars in the cybersecurity industry. Most market projections say the industry is worth about $180 billion. About 15 percent of that market goes to data security. But all the indications are that we are losing the war in personal identity security That leaves is with the question: Do corporations really care about customer security?
Probably not
US Department of Health and Human Services reported recently that. in the US, there have been 2,213 breaches since 2020, with 152.1M affected individuals. That is almost half of the American population. But that is just breaches involving medical data.
The FBI reports, in the same period, more than 350 million stolen personal information records, exceeding the known population of the country. Worldwide, the number of personal identity information (PII) records exceeds one billion people.
So how bad is it? “I always tell people assume your social security number has been breached. Just assume that,” said John Meyer, senior director for Cornerstone Advisors, an organization providing security consultation to financial organizations.
So we are spending tens of billions of dollars to protect data from exfiltratation on almost a weekly basis from attacks bypassing current defenses. Is it worth the investment? Does protecting that data even matter?
Well, yes… sort of
Data security professionals say it is and it does. Communications, industry intellectual property, state secrets, and control of crucial systems must still be protected. Most professionals we talked to cite ransomware attacks as the primary reason for investing in security precuts and services.
Highly Effective AI-Enabled Cybersecurity Requires Massive Amounts of Data
Becoming an expert cybersecurity solution using AI requires processing and analyzing massive amounts of data over time to understand the nuances of how it’s being used for malicious purposes. Data, how it is collected, stored, and analyzed, and the insights gained are essential to successfully protecting, detecting, and responding to cybersecurity threats.

Election security is not a technology problem. It is how naive we are
When it comes to election security, the technology we use to vote and count those votes is not the problem. The problem is how naive we are.
Election security has been at the forefront of daily news cycles for more a decade. The concerns about illicit use of technology to input and count the votes turned out to be largely overblown. Every U.S. state other than the Commonwealth of Louisiana, uses paper ballots, matching the practice of every other western democracy. Lawsuits have bankrupted people and organizations claiming the technology was changing votes. Those that have complained the loudest about election interference are now facing prosecution for the crimes.
Now the tech focus is on the use of artificial Intelligence to create deepfake video and audio. A recent pitch from Surfshark,
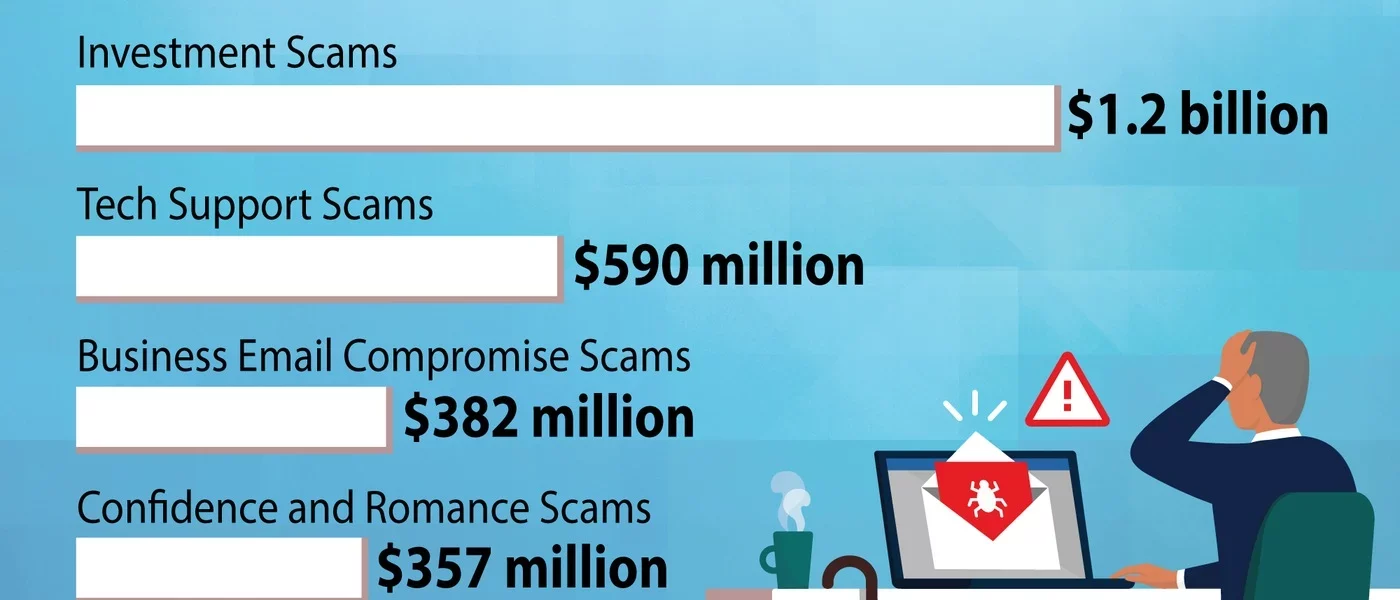
Elder fraud festers out of control
As legislatures around the world try to get a handle on the growth of ransomware, another category of cybercrime is festering out of control: Elder fraud.
The FBI’s Internet Crime Complaint Center (IC3) reported more than 100,000 people in the US, 60 years and older, lost $3.4 billion total to digital scams. The IC3 pointed out that the elderly are half as likely to report a loss. So the actual crimes and losses are probably much higher.
In contrast, the total ransomware payouts last year from reporting companies was $1.1 billion according to Chainanalysis. While the total number of fraud reports to the IC3 appears to have leveled off after years of growth, elder fraud increased by 14 percent year on year.
“Combatting the financial exploitation of those over 60 years of age continues to be a priority of the FBI,” wrote FBI Assistant Director Michael D. Nordwall, who leads the Bureau’s Criminal Investigative Division, in the report. “Along with our partners, we continually work to aid victims and to identify and investigate the individuals and criminal organizations that perpetrate these schemes and target the elderly.”
Who is vulnerable?
Info-sec.live Weekly News Show with Rohit Ghai
Identity security is one of the most significant issues facing individuals and businesses. Phishing and identity theft dwarfs ransomware in…more...
Free Membership Required
You must be a Free member to access this content.
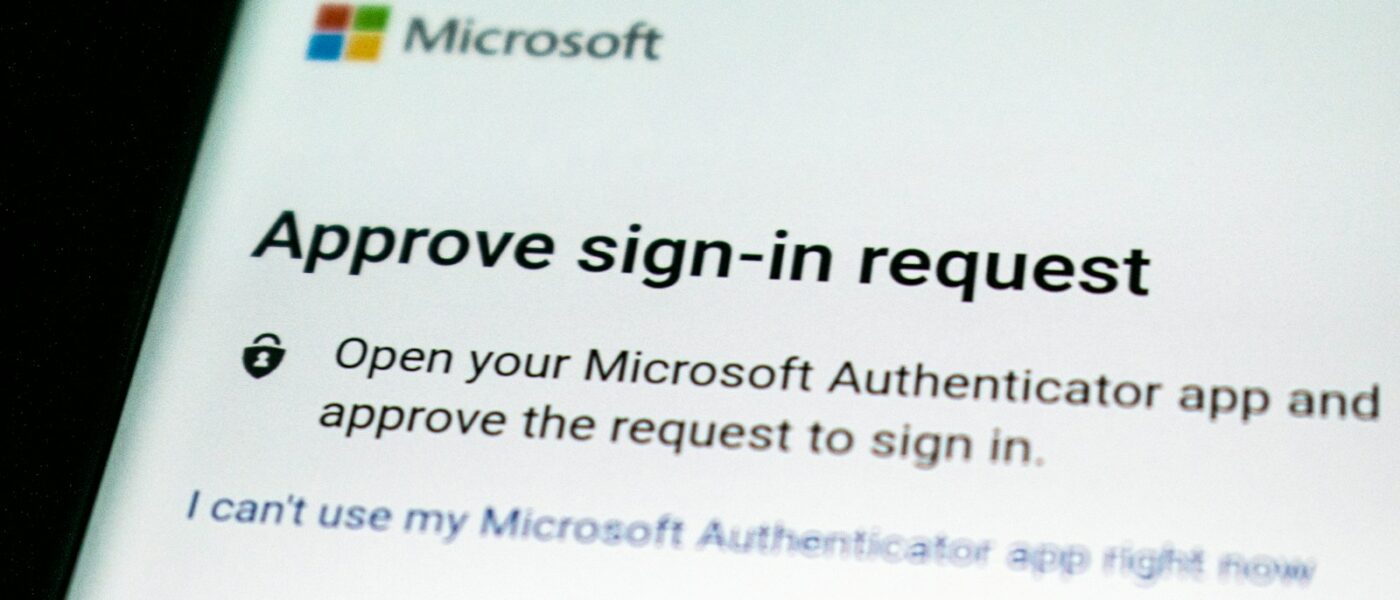
Reinforcing Multi Factor Authentication
As the password slowly abdicates to a new heir, which specific alternatives are shaping up to take its place? Multi-factor authentication (MFA) has been rapidly adopted by organizations to help reduce the opportunities for breaches. But MFA brings its own considerations that must be addressed.

Mining data is daunting but crucial
The cybersecurity industry seems addicted to research but isn’t all that good at it. Mining the massive amount of data produced is daunting but crucial to everyone.
Surveys and studies are an important part of marketing form the cybersecurity industry. Cyber Protection magazine receives a lot of them. We read them all. In the two months before the RSA Conference, more than one a day came into our inbox. However, they are not a great source of independent data and insight.
Ignoring the cherry-picked data highlighting a particular company’s product or service, there are a few nuggets that, taken together, produce some interesting insights. Out of 60+ reports, we took a pass on any that were repetitive, were suspect methodologically, or effectively plagiarized from another source. We chose to look at seven with a solid methodology, representation of industry-wide concerns, and originality. The reports came from Dynatrace, Black Kite, SlashNext, Metomic, Originality AI, Logicgate, and Sophos. We found three common themes: The impact of AI on security, government regulation compliance, and understanding of security concerns on the C-suites and board levels.
Understanding security issues.
Almost every study has a common complaint. CISOs say application security is a blind spot at the CEO and board levels. They say increasing the visibility of their CEO and board into application security risk is urgently needed to enable more informed decisions to strengthen defenses.
However, Dynatrace’s study said CISOs fail to provide the C-suite and board members with clear insight into their organization’s application security risk posture. “This leaves executives blind to the potential effect of vulnerabilities and makes it difficult to make informed decisions to protect the organization from operational, financial, and reputational damage.”
Recent news shows the study may have a point. Marriott Hotels admitted that a 2018 breach was the result of inadequate encryption of customer data. In 2018 the company claimed their data was protected by 128-bit AES encryption when customer identity was only protected by an outdated hashing protocol. One can imagine the discussion between the CEO and the IT department:
CEO: is our data encrypted?
IT manager: Yeah, sort of.
CEO: OK, good enough
If the CEO doesn’t understand the difference between a hash and AES encryption, that’s a problem.
And there many be evidence that ignorance is widespread. Apricorn reported that the number of encrypted devices in surveyed companies had dropped from 80 percent to 20 percent between 2022 and 2023. Some of that could be attributed to work-from-home (WFH) growth in companies. It is also likely that companies over-reported what was encrypted simply because they did not understand what “encryption” meant. Once they learned the meaning, adjustments were made.
That lack of a foundational security technology could be a reason for the devastating growth in ransomware in the past two years.

RSAC Reporter’s Notebook: Change is coming
The cybersecurity industry is just absolute chaos, and rightly so. This is the industry charged with plugging dikes during the Class-5 hurricane that the internet seems to be today. Nowhere is that chaos more evident than at RSAC just from a marketing perspective. Everyone has “ground-breaking”, “industry-leading”, and “first ever” product offerings and this year was no different. But if you can look past the Macho-man impersonations, Formula One cars, and the mesmerizing miasma of the website and show floor, you can see an order forming in the chaos. Change is coming.
Back to step one
RSA CEO Rohit Ghai, said we have missed a step in AI development. “We’ve seen it first as a co-pilot alongside of a human pilot and then see it taking over flying the plane.” He said the first step is making it an advanced cockpit making it easier for less trained and experienced people to do the work. He pointed out that cybersecurity is an industry with negative employment making it difficult to find experienced technicians to do the work.
Last year, any discussion of ethical development was met with confused stares. This year, the need for ethical AI development is taken seriously but few can see a profit in it. Cybersecurity VC Rob Ackerman (DataTribe) and Carmen Marsh, CEO of the United Cybersecurity Alliance, were open to suggestions,
“From the perspective of (companies like OpenAI), I understand the reasons to go as fast as they can to develop a true artificial intelligence, the question is, who are the people in the room guiding the process?” said Ackerman. “Once you get a diverse set of advisors working on the problem, then you do the best you can to create something ethical. But right now, we aren’t even doing the best we can.”
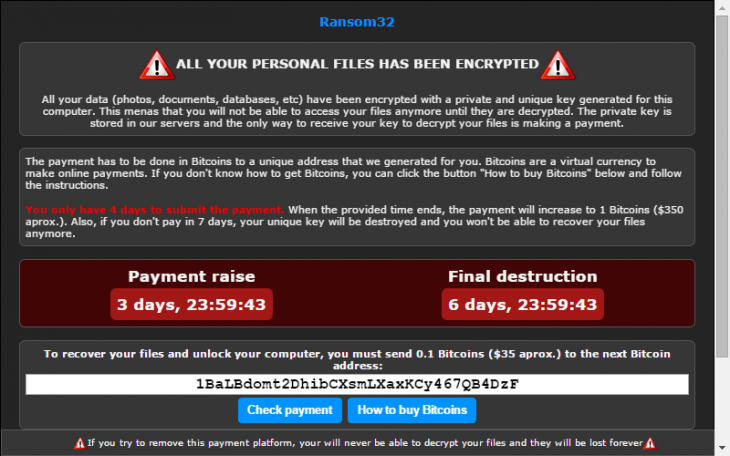
How to stop ransomware in its tracks
The name WannaCry still invokes memories of chaos and disaster amongst anyone in the technology world. The anniversary of this widespread attack in May each year has been named Anti-Ransomware Day, to encourage organisations to back up their data and adopt necessary security protections.

Third-party security is almost impossible
There are many themes arising for the RSA Conference next week including tools and services to protect against originating with unsecured third parties in the supply chain. That is a crucial issue in every industry especially with almost every company doing business with a supplier in the cloud. But the scope of the problem is almost impossible to resolve. The reasons are myriad.
With every Fortune 1000 business and government agency doing business with tens of thousands of third-party suppliers, the odds of finding one chink in the security protocols are very good for the criminals and state actors looking to do damage.
Social engineering can easily bypass the strongest technical defenses. It only takes a single lapse in digital hygiene to open the door to man-in-the-middle attacks, invite malware injections, and launch credential stuffing. It is also the favorite strategy of ransomware gangs.
Ransomware grabs headlines and remains highly lucrative for ransomware gangs. When compared to other forms of cybercrime, however, ransomware is really a minor issue. There are more than 33 million small businesses (under $100 million in revenue) operating in the United States alone representing 99 percent of all businesses. However, according to a study produced by the Black Kite Research and Intelligence Team, less than 5000 of them experienced a successful ransomware attack in the last 12 months...

Passwordless Instead of Password Security
In 2013, Intel launched World Password Day to raise awareness of the relevance of secure passwords – with limited success. Today we might be at the brink of finally saying goodbye to password.

Scam Bucket: Credit card fraud is inevitable
You can do everything right, but credit card fraud is inevitable.
In recent weeks, Cyber Protection Magazine has fielded calls and emails from people who have followed all the best-known techniques for securing banking, debit, and credit card information. That includes bank notifications every time the card is used, multi-factor authentication (MFA), biometrics, and limiting the use of a card for specific transactions. These readers still experienced unauthorized use of their payment cards
How does that happen?
The market for criminal use of legitimate credit cards is a well-known “secret.” The most common sites are found on the DarkWeb, but occasionally they pop up on Meta sites, where they can reap thousands of dollars before Meta gets around to kicking them off, generally without prosecution.
The criminals collect most of this information through phishing attacks using email, but also on Facebook and Instagram, and falling for a phishing scam may negate victims’ claims they “did everything right.” Criminals, however, are getting more sophisticated. Enterprises selling the card information gather it by sending fraudulent emails or text messages, posing as legitimate entities, and tricking individuals into providing their credit card information. Then there is basic social engineering, manipulating victims into revealing their credit card information through phone calls, and QR codes.
Even more sophisticated, criminals will install skimming devices on ATMs, gas pumps, or point-of-sale terminals to capture credit card information when cards are swiped or inserted. While it may not be obvious that the skimmers have been added to the terminal, it is fairly easy to determine if it is legitimate. Legitimate card readers cannot be easily removed, while skimmers may be held on with a simple adhesive. Some locations, like Costco fueling stations, place tape over the reader and, if broken, can alert users and the vendor that there may have been a breach.
No one is completely safe
But by and large, data breaches are the most common source of stolen credit card information, and that is something most victims cannot do anything about.
By hacking into databases of companies or financial institutions criminals steal terabytes of credit card information. Employees of companies or financial institutions may access and sell credit card information, posting the information of those above, carding forums. Criminals exchange...
Purchase Required
This content requires that you purchase additional access. The price is $1.00 or free for our Premium members.

Like Digital Cicadas, Cybercriminals Lie In Wait Before Unleashing Their Presence
A curious parallel can be drawn between cybercriminals and the intriguing phenomenon of Cicadas. Akin to the periodic insects that emerge from the ground after years of dormancy, cybercriminals often resurface with renewed vigor, unleashing their disruptive activities on unsuspecting organizations.
Purchase Required
This content requires that you purchase additional access. The price is $1.00 or free for our Premium members.

Turning the corner on cyber insurance
It seems like the insurance industry is turning the corner on cyber insurance and making a decent profit in the process. But not every industry watcher is optimistic.
Purchase Required
This content requires that you purchase additional access. The price is $1.00 or free for our Premium members.


